我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
使用亚马逊 OpenSearch Service 托管 VPC 终端节点简化解决方案的私有网络访问
该功能是使用 亚马逊云科技 PrivateLink 构建的。亚马逊云科技 PrivateLink 在 VPC、支持的 亚马逊云科技 服务和您的本地网络之间提供私有连接,而不会将您的流量暴露给公共互联网。它为您提供了将多个应用程序部署毫不费力地连接到您的亚马逊 OpenSearch Service 域的方法。
这篇文章介绍了建立在 亚马逊云科技 PrivateLink 之上的亚马逊 OpenSearch 服务托管 VPC 终端节点,并展示了如何使用亚马逊 OpenSearch Service 管理的 亚马逊云科技 PrivateLink 从托管在同一个账户中的一个或多个 VPC 访问私有亚马逊 OpenSearch 服务,甚至是托管在其他亚马逊云科技账户中的VPC。
亚马逊 OpenSearch Service 托管 VPC 端点
在 Amazon OpenSearch Service 托管 VPC 终端节点启动之前,如果您需要在 VPC 之外访问您的域名,则有三种选择:
- 使用 VPC 对等连接将您的 VPC 与其他 VPC 连接起来
- 使用 亚马逊云科技 Transit Gateway 将您的 VPC 与其他 VPC 连接起来
- 创建您自己的 亚马逊云科技 私有链接设置实现方案
前两个选项要求您设置 VPC,以使无类域间路由 (CIDR) 区块范围不会重叠。如果他们这样做了,那么你的选择就会更加复杂。第三个选项是
有了亚马逊 OpenSearch Service 托管 VPC 终端节点(即由 亚马逊云科技 PrivateLink 提供支持),不再需要这些复杂的设置和流程!
您可以访问您的 Amazon OpenSearch Service 私有域,就好像它已部署在您想要连接到您的域的所有 VPC 中一样。如果您需要通过本地混合部署进行私有连接,那么 亚马逊云科技 PrivateLink 可以帮助您轻松地将访问从亚马逊 OpenSearch Service 域传送
通过将 亚马逊云科技 PrivateLink 与亚马逊 OpenSearch 服务结合使用,您可以获得以下好处:
- 您可以简化混合、多 VPC 和多账户解决方案之间的网络架构
- 通过更好地控制解决方案和亚马逊 OpenSearch Service 域名之间的流量,您可以解决大量合规问题
适用于多个开发团队的共享搜索集群
假设贵公司托管的服务即软件 (SaaS) 应用程序为医疗保健行业提供搜索应用程序编程接口 (API)。每个团队都在 API 的不同功能上工作。开发 团队 API 小组 1 和 API 小组 2 位于两个不同 的 亚马逊云科技 账户中,每个账户中都有自己的 VPC。另一个团队( 数据优化小组 )负责 提取和数据优化,以填充托管在与 API 小组 2 相同的账户 中但在 VPC 中不同的 Amazon OpenSearch Service 域。在开发周期中,每个团队共享域名,以节省成本并促进数据建模方面的协作。
解决方案概述
自行管理的 亚马逊云科技 私有链接架构,用于连接不同的 VPC
在这种情况下,在亚马逊 OpenSearch Service 管理 VPC 终端节点(即由 亚马逊云科技 PrivateLink 提供支持)之前,您必须创建以下项目:
- 在您的 VPC 中部署 NLB
- 创建一个指向弹性网络接口 (ENI) IP 地址的目标组,该地址由亚马逊 OpenSearch 服务在您的 VPC 中创建并用于启动亚马逊 OpenSearch 服务
- 创建 亚马逊云科技 PrivateLink 部署并引用您新创建的 NLB

在您实施 NLB 时,
通常,客户在
使用新的简化网络架构,您的团队将完成以下步骤。
OpenSearch 服务托管 VPC 端点架构(由 亚马逊云科技 PrivateLink 提供支持)
由于 Amazon OpenSearch Service 负责处理前面描述的基础设施,但不一定采用 相同的实现方式,因此您真正需要注意的是按照
完成说明中的步骤并删除自己的实现后,您的架构将得到简化,如下图所示。
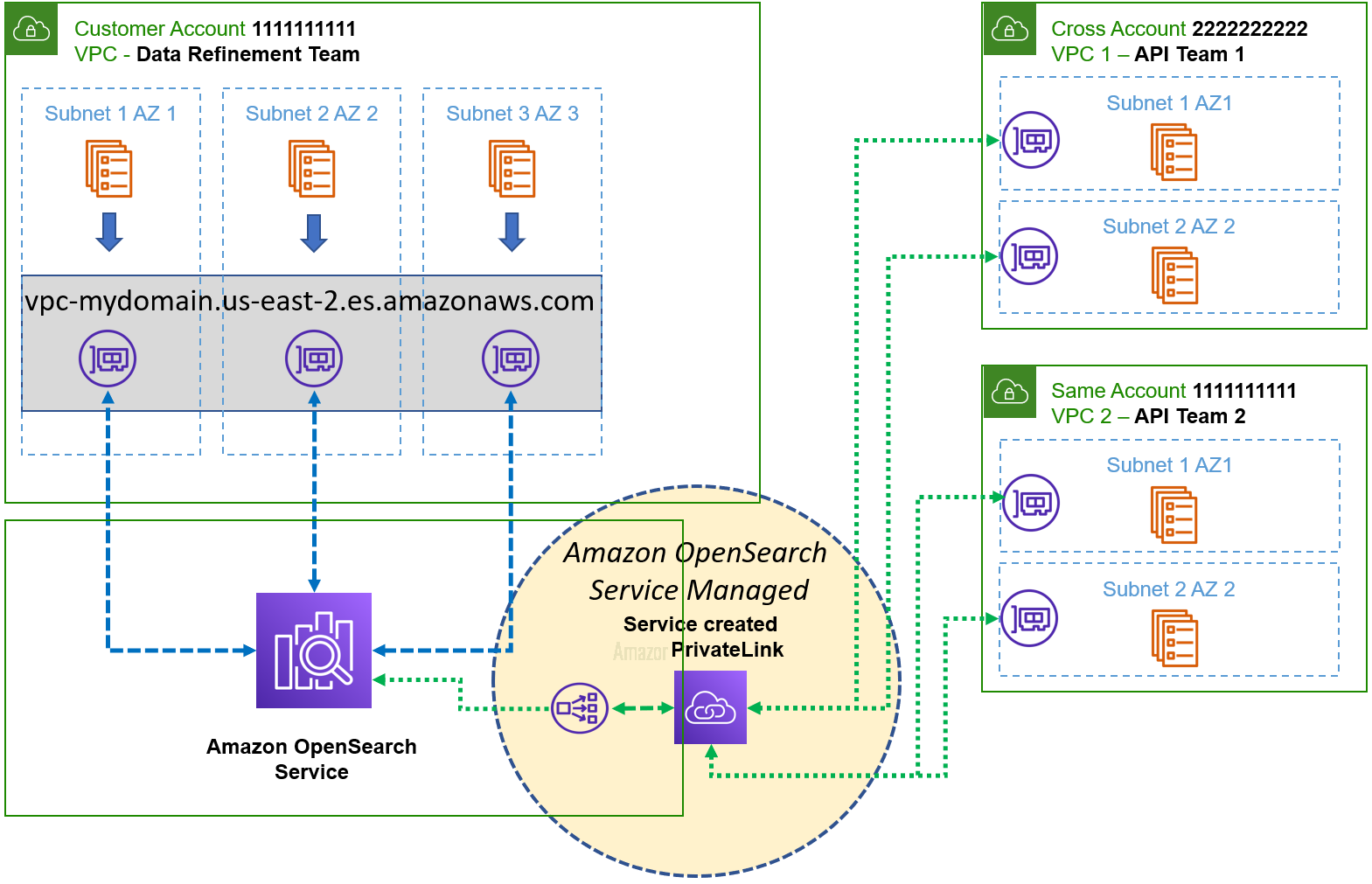
此时,开发团队( API 小组 1 和 API 小组 2 )可以通过亚马逊 OpenSearch Service 托管 VPC 终端节点访问亚马逊 OpenSearch 集群。此选项具有高度的可扩展性,其简化的网络架构使您不必担心管理 NLB 或设置目标组和其他资源。如果将来开发团队和 VPC 的数量增加,则可以将域与关联的接口 VPC 终端节点关联起来。即使存在重叠的 CIDR Block IP 范围,您也可以使用相同或不同的账户访问 VPC 中的服务。
结论
在这篇文章中,我们介绍了使用 OpenSearch 服务管理的 VPC 终端节点 (亚马逊云科技 PrivateLink) 从不同的 VPC 跨不同账户访问 Amazon OpenSearch 集群的架构设计。使用传输网关、自行管理的 亚马逊云科技 PrivateLink 或 VPC 对等连接需要复杂的联网策略,这会增加运营负担。随着 Amazon OpenSearch Service 的 VPC 终端节点的引入,您的解决方案的复杂性大大简化了,更好的是,它可以为您管理!
作者简介


*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。