我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
使用 Amazon S3 存储桶密钥将 亚马逊云科技 密钥管理服务的成本降低多达 99%
许多行业的客户在数据安全和隐私方面面临着越来越严格的审计和合规要求。某些合规框架,例如FISMA、FEDRAMP、PCI DSS和SOC 2,有用于验证系统安全的特定监管标准。对这些合规框架的共同要求是对静态数据采用更严格的加密标准,组织必须使用他们控制的加密密钥对数据进行加密。为了在本地满足这些要求,客户必须投入专用资源来维护加密模块。在云中,客户使用根据使用量定价的加密产品。
除非客户选择其他类型的服务器端 加密,否则@@
在这篇文章中,我将向您展示如何要求写入存储桶的所有对象使用 SSE-KMS,如何在存储桶上启用 S3 存储桶密钥,如何在多租户存储桶中使用 S3 存储桶密钥,以及如何评估通过对象级 SSE-KMS 加密的现有对象。使用 S3 存储桶密钥可以帮助您节省 亚马逊云科技 KMS 账单,同时仍符合使用 SSE-KMS 加密数据的安全要求。
背景
SSE-KMS 为客户提供了对其加密密钥的控制以及审核密钥使用情况的能力。这些额外的控制措施对于必须向审计员证明其加密密钥的所有权、对密钥轮换计划的控制以及加密密钥权限的管理的企业客户非常重要。使用 SSE-KMS 加密对象时,亚马逊云科技 KMS 会收到来自 Amazon S3 的加密请求,并发回一个唯一的数据密钥来加密该对象。
使用 S3 存储桶密钥,亚马逊云科技 KMS 会生成一个有时间限制的存储桶级密钥,而不是单独调用 亚马逊云科技 KMS 来加密每个对象。Amazon S3 使用此存储桶级密钥创建唯一的数据密钥来加密存储桶中的对象,从而无需额外的 亚马逊云科技 KMS 请求即可完成加密操作。S3 存储桶密钥减少了从 Amazon S3 到 亚马逊云科技 KMS 的请求流量,使您能够访问亚马逊 S3 中的加密对象,而费用仅为之前的一小部分。
先决条件
要关注博客文章,您的
Minimum IAM permissions to use Bucket Keys
{
"Version":"2012-10-17",
"Statement":[
{
"Sid": "Permissions to use Bucket Keys",
"Effect":"Allow",
"Principal": {"AWS": "arn:aws:iam::111122223333:user/willcavin"},
"Action":[
"s3:PutObject",
"s3:GetObject",
"s3:CreateBucket",
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource":"arn:aws:s3:::willcavinbucket/*"
}
]
}
图 1:使用 S3 存储桶密钥的 IAM 权限示例
写入存储桶的所有对象都需要 SSE-KMS
有合规性要求的客户通常希望要求对上传到其 S3 存储桶的所有对象使用 SSE-KMS 进行加密。这可以通过
{
"Version": "2012-10-17",
"Id": "PutObjPolicy",
"Statement": [{
"Sid": "DenyObjectsThatAreNotSSEKMS",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::example-bucket/*",
"Condition": {
"Null": {
"s3:x-amz-server-side-encryption-aws-kms-key-id": "true"
}
}
}]
}图 2:启用 S3 存储桶密钥的 IAM 权限示例
在存储桶上启用 S3 存储桶密钥
通过编辑存储桶上的默认加密,可以通过 Amazon S3 控制台启用 S3 存储桶密钥。选择存储桶后,选择 属性 。在 “ 默认加密 ” 下 ,选择 “编辑” 。
在 加密密钥类型 下 ,选择 亚马逊云科技 密钥管理服务密钥 (SSE-KMS )。 在 亚马逊云科技 KMS 密钥 下 ,选择您的首选 亚马逊云科技 KMS 密钥。在 “ 存储桶密钥 ” 下 ,选择 “ 启用 ” 。选择 “ 保存更改 ” 。
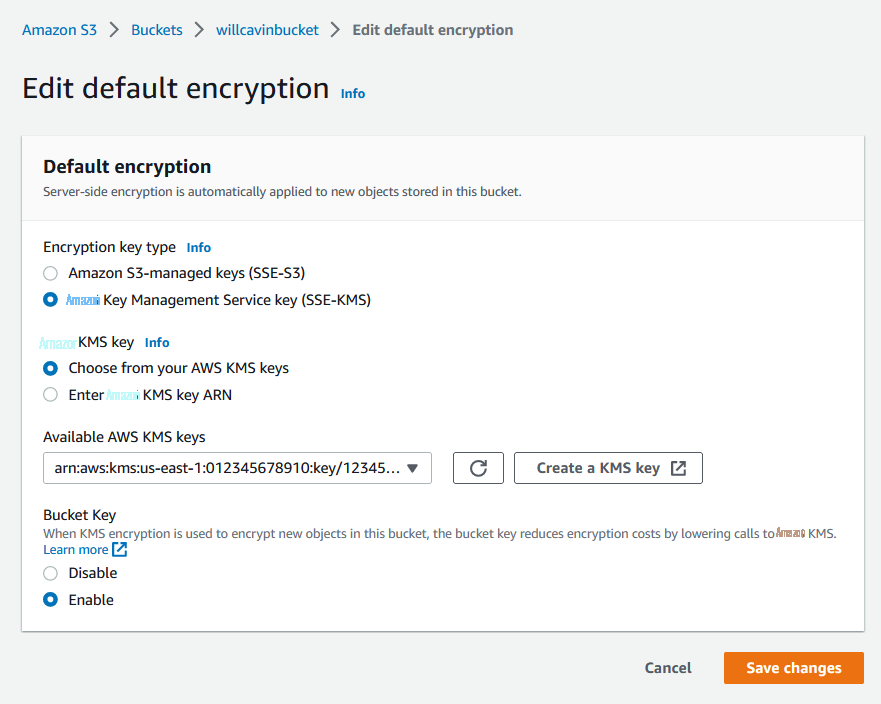
图 3:启用 S3 存储桶密钥的默认加密配置示例
使用 亚马逊云科技 命令行界面
aws s3api put-bucket-encryption --bucket <bucket-name> --server-side-encryption-configuration '{
"Rules": [
{
"ApplyServerSideEncryptionByDefault": {
"SSEAlgorithm": "aws:kms",
"KMSMasterKeyID": "<KMS-Key-ARN>"
},
"BucketKeyEnabled": true
}
]
}'请注意,Amazon S3 为添加到您的存储桶的新对象启用 S3 存储桶密钥。现有对象不使用 S3 存储桶密钥。
在多租户环境中使用 S3 存储桶密钥
许多客户在多租户场景中使用 S3 存储桶,他们可能有多个团队或最终客户将对象上传到共享存储桶进行分析或数据处理。S3 存储桶密钥旨在在此模型中使用。您只需在存储桶默认加密配置中启用 S3 存储桶密钥,然后让您的最终客户将其首选的客户管理的 亚马逊云科技 KMS 密钥添加到其 Amazon S3 请求标头中。这允许最终客户使用其客户管理的 亚马逊云科技 KMS 密钥加密对象,并使多租户存储桶所有者能够为上传到其存储桶的对象启用 S3 存储桶密钥。
在此结构中,每个租户都与您共享其客户管理的 亚马逊云科技 KMS 密钥,因此您可以执行服务(数据分析、数据处理等)。如果租户决定他们不再希望你访问他们的数据,那么他们只需删除你对他们的密钥的访问权限。该模型在为相关方提供访问权限的同时,保持了关键材料的机密性。
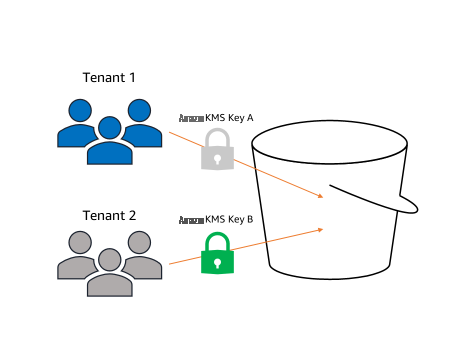
图 4:使用 亚马逊云科技 KMS 密钥的多租户存储桶示例
使用 SSE-KMS 对象评估读取密集型存储桶
自 S3 存储桶密钥推出以来,许多客户已重新加密现有数据以采用存储桶密钥并降低其 亚马逊云科技 KMS 成本。如果您有一个读取密集型存储桶,其中包含通过对象级 SSE-KMS 加密的对象,则应仔细评估访问模式,看看这对您的应用程序是否有意义。您可以使用 S3 Storage Lens 识别您
要使用 S3 存储桶密钥加密您现有的 Amazon S3 对象,您可以使用 Amazon S3 批量操作。您为 S3 批处理操作提供对象列表,批处理操作会对每个对象执行指定的操作。您可以使用
要知道的事情
许多客户通常希望在未启用 S3 存储桶密钥的情况下快速审核其账户的存储分区默认加密配置。这
启用 S3 存储桶密钥之前需要注意的更改
如果您现有的 IAM 策略或 亚马逊云科技 KMS 密钥策略使用您的对象 A
启用 S3 存储桶密钥后,您会在日志中看到的 SSE-KMS 对象的 亚马逊云科技 KMS CloudTrail 事件较少,因为对 亚马逊云科技 KMS 的调用较少。此外,您的 亚马逊云科技 KMS CloudTrail 事件会记录您的存储桶 ARN,而不是您的对象 ARN。
使用复制 API
您可以使用 “复制” 操作来重新加密现有对象。请注意,复制操作会更改对象的上次修改日期,如果您制定了生命周期规则,则会重置对象的生命周期资格。或者,您可以在 “复制” 操作期间添加新的对象标签,以追溯识别重新加密的对象。然后,您可以创建新的生命周期规则,将这些标记的对象转移到较冷的存储空间或自行决定过期。此外,任何大于 5 GB 的对象都必须
正在清理
如果您创建了新资源来测试本文中分享的建议,请删除您的客户管理的 亚马逊云科技 KMS 密钥以及您添加到存储桶中的所有对象。
结论
许多客户都有合规性要求,要求客户控制其加密密钥,这些客户使用带有客户管理密钥的 SSE-KMS 来遵守这些监管标准。在这篇博客文章中,我们了解了如何使用 S3 存储桶策略在存储桶级别强制执行 SSE-KMS 加密。我们还了解了如何在默认存储桶加密配置中启用 S3 存储桶密钥,以便轻松利用这项节省成本的功能。我们讨论了多租户存储桶所有者如何启用 S3 存储桶密钥,同时仍允许其客户使用他们自己的客户管理的 KMS 密钥。最后,在重新加密现有 SSE-KMS 对象以使用 S3 存储桶密钥之前,我们回顾了一些重要的访问模式注意事项。
对于有数据加密合规性要求的客户,建议启用 S3 存储桶密钥的最佳做法。此功能可以节省您的
感谢您阅读此博客,如果您有任何意见或疑问,请随时将其留在评论部分。
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。