我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
使用亚马逊 Athena 联合查询查询跨账户的亚马逊 DynamoDB 表
如果您需要允许其他 亚马逊云科技 账户查询您的 DynamoDB 表怎么办?如果其他账户需要将您的 DynamoDB 表上的数据与存储在亚马逊 CloudWatch、Amazon DocumentDB、亚马逊 Redshift、Amazon OpenSearch、MySQL、连接雅典娜数据源
这篇文章将演示 Aws 账户中的 Athena 使用 Athena 跨账户联合查询访问另一个 亚马逊云科技 账户的 DynamoDB 表。它还解释了 使用 A
草率排练
该解决方案包含以下步骤来演示 Athena 跨账户联合查询:
- 设置 Athena 联邦 -为数据源连接器部署 Lambda 函数并将其连接到数据源。
- 设置 Athena 跨账户联合 -为 Athena 跨账户联合 设置 IAM 权限。
- 测试 Athena 跨账户联合查询 — 演示一个 亚马逊云科技 账户如何与另一个 亚马逊云科技 账户共享其 DynamoDB 表作为雅典娜数据源。
先决条件
在本演练中,您应该具备以下先决条件:
- 两个 亚马逊云科技 账户
- 亚马逊云科技 资源:亚马逊 Simple Storage Service(亚马逊 S3)、亚马逊 Athena、亚马逊 DynamoDB、Aws Lambda
数据源连接器
数据源连接器是一段可以在目标数据源和 Athena 之间转换的代码。雅典娜使用在 亚马逊云科技 Lambda 上运行的数据源连接器来运行联合查询。你可以将连接器视为 Athena 查询引擎的扩展。
连接器使用 Apache Arrow 作为返回查询中请求的数据的格式,这使连接器可以用 C、C++、Java、Python 和 Rust 等语言实现。
雅典娜使用在 亚马逊云科技 Lambda 上运行的数据源连接器来运行联合查询。由于连接器是在 Lambda 中处理的,因此它们可用于访问可从 Lambda 访问的云端或本地的任何数据源的数据
要在您的 Athena 查询中使用连接器,请使用以下方法之一将其部署到您的账户:
-
亚马逊云科技 Serverless 应用程序存储库 - 雅典娜和 Lambda 游戏机
本博客使用
部署数据源连接器后,该连接器将与您可以在 SQL 查询中指定的目录相关联。您可以使用单个查询组合来自多个目录的 SQL 语句并跨越多个数据源。当针对数据源提交查询时,Athena 会调用相应的连接器来识别表中需要读取的部分、管理并行度并下推过滤谓词。根据用户提交的查询,连接器可以提供或限制对特定数据元素的访问权限。
架构
-
AWS 账户 A 有一张名为 Music 的 DynamoDB 表。 - 账户 A 有一个 Athena 数据源连接器,可以联合到 DynamoDB 中。
- 亚马逊云科技 Account-B 的分析师需要查询 DynamoDB 表。
- 账户 A 使用雅典娜跨账户联合查询与账户 B 共享 Athena 数据源。
下图显示了账户 B 使用亚马逊 Athena 跨账户联合访问账户 A 中的 DynamoDB。

要演示 Athena 跨账户联合,请在账户 A 中创建名 为音乐的 DynamoDB 示例表。
按照
音乐
表 并加载
样本数据。
成立雅典娜联邦
创建联合查询的准备过程分为两部分:为数据源连接器部署 Lambda 函数,以及将 Lambda 函数连接到数据源。有关更多详细信息,请参阅
使用 亚马逊云科技 Serverless 应用程序存储库部署 AthenadynamodbConnector
- 以管理员身份登录 亚马逊云科技 账户 A。
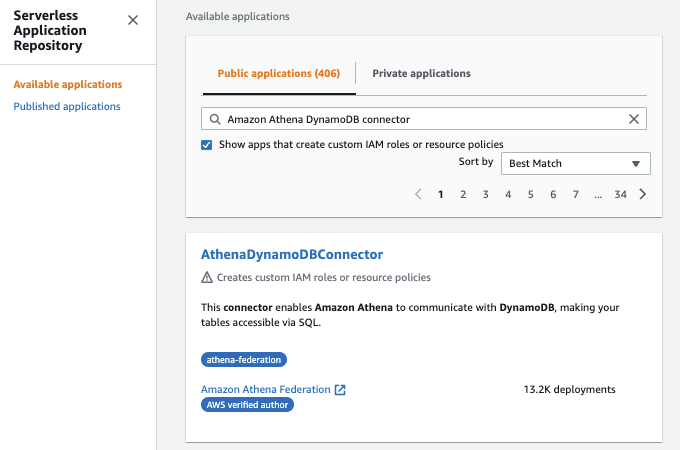
- 打开 无服务器应用程序存储库 。
- 在导航窗格中,选择 可用应用程序 。
- 选择 “ 显示创建自定义 IAM 角色或资源策略的应用程序 ” 选项 。
-
在搜索框中,键入连接器的名称 A
thenadynamodbConnector。
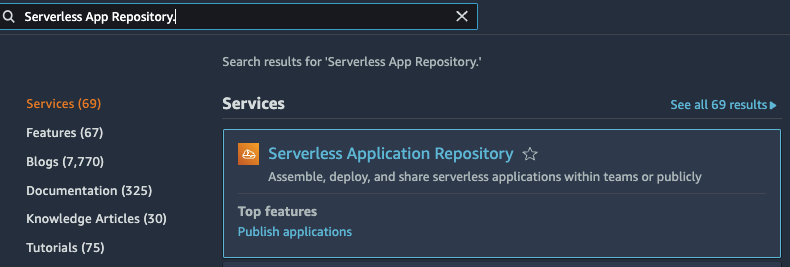
- 选择连接器会在 亚马逊云科技 Lambda 控制台中打开 Lambda 函数的 应用程序详情 页面。
-
在详细信息页面的右侧,对于
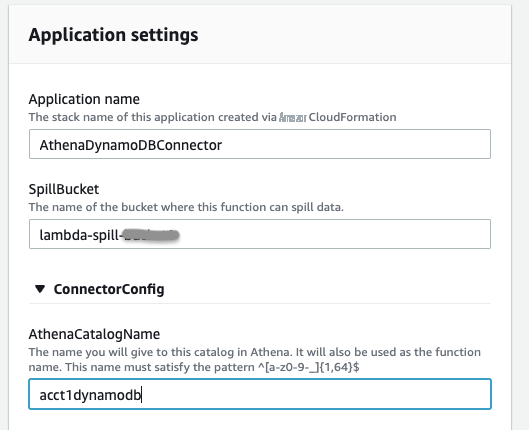
“ 应用程序设置”
,填写必填信息。
-
应用程序名称
— 用于部署连接器的 AWS CloudFormation Stack 的名称: AthenadynamodbConnector。
A
-
thenaCatalogname
— 这是要在 Athena 中创建的目录名称。它也是 Lambda 函数的名称。
用小写字母给出:acct1dynamodb 。 -
SpillBucket
— 指定您的账户中现有的 S3
存储桶(溢出存储桶),以便从任何超过 Lambda 函数响应大小限制的大型响应负载接收数据。
-
应用程序名称
- 选择 “ 我确认此应用程序创建自定义 IAM 角色和资源策略 ” 。要了解更多信息,请选择 “ 信息 ” 链接。
- 在 应用程序设置 部分的右下角,选择 部署 。
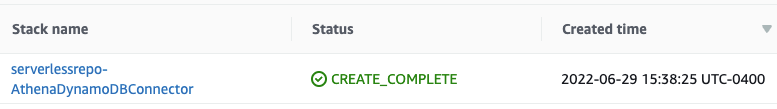
- 无服务器应用程序存储库 将创建一个 亚马逊云科技 CloudFormation 堆栈来部署连接器。
-
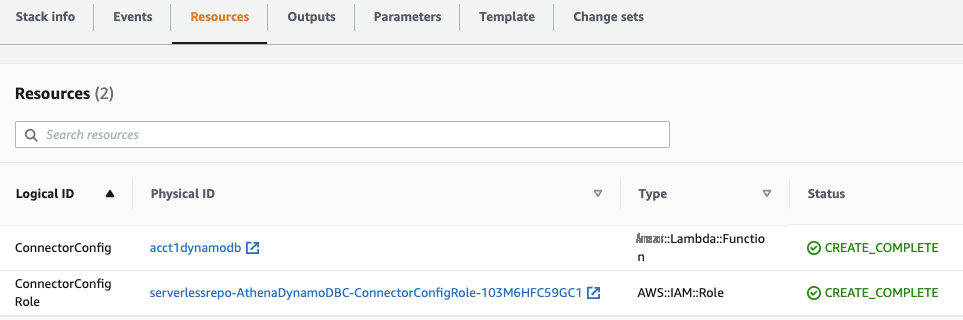
部署完成后,您将在亚马逊云科技 CloudFormation堆栈的
资源
部分看到 Lambda 函数。记下 Lambda 函数的名称。
将 Athena 连接到数据源
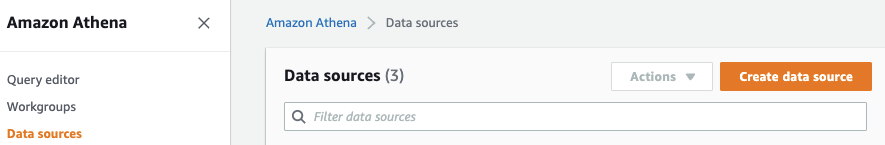
- 在账户 A 中进入雅典娜控制台。
-
选择数据源。单击 “创建数据源”。
-
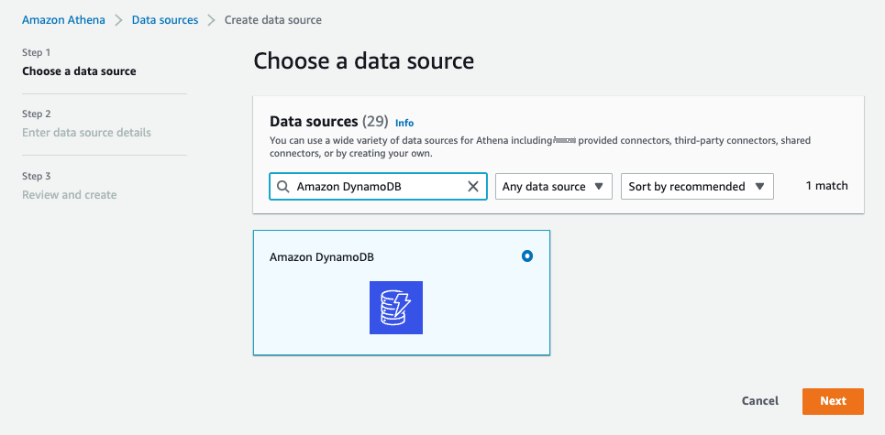
在选择数据源中,搜索亚马逊 DynamoDB 并将其选中。
-
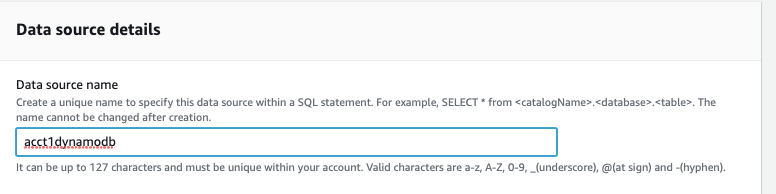
在
数据源详细信息
中 ,给出一个
数据源名称
acct1dynamodb
-
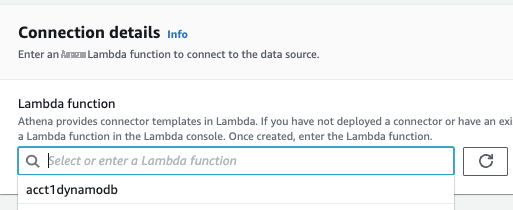
对于
连接详细信息
部分中的
Lambda 函数
,从下拉列表中选择函数的名称
acct1dynamodb。
-
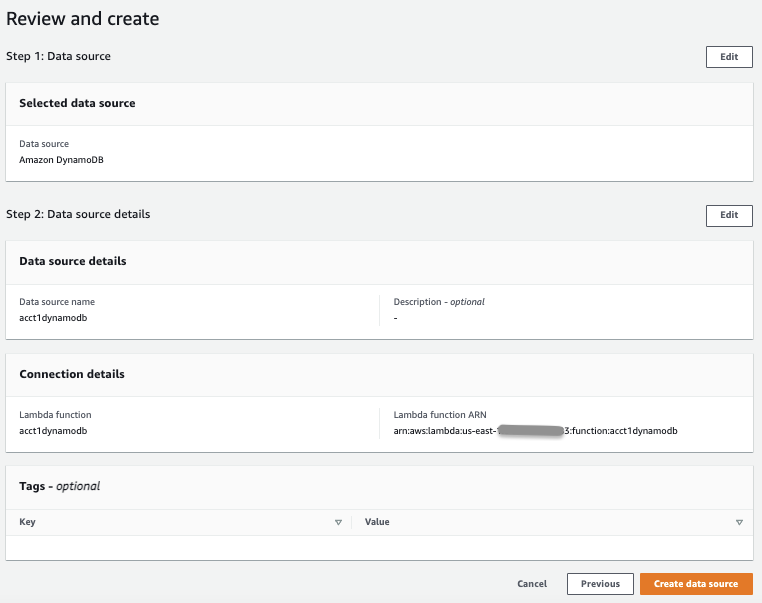
在 “
查看并创建
” 页面上,查看数据源详细信息,然后选择 “
创建数据源
” 。

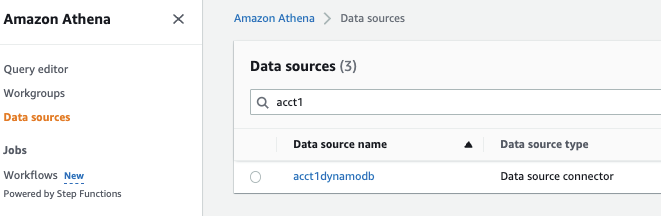
-
你将在数据源中看到数据源
acctdynamodb。
-
转到
查询编辑器
。从下拉列表中选择
数据源
acct1dynamodb。
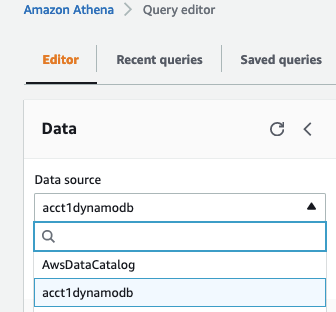
-
您将看到共享数据源中的所有表。
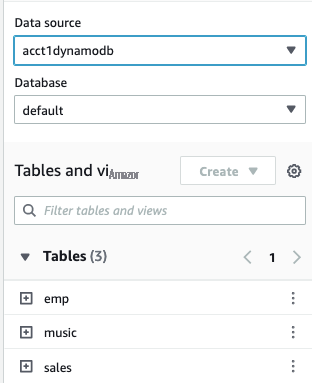
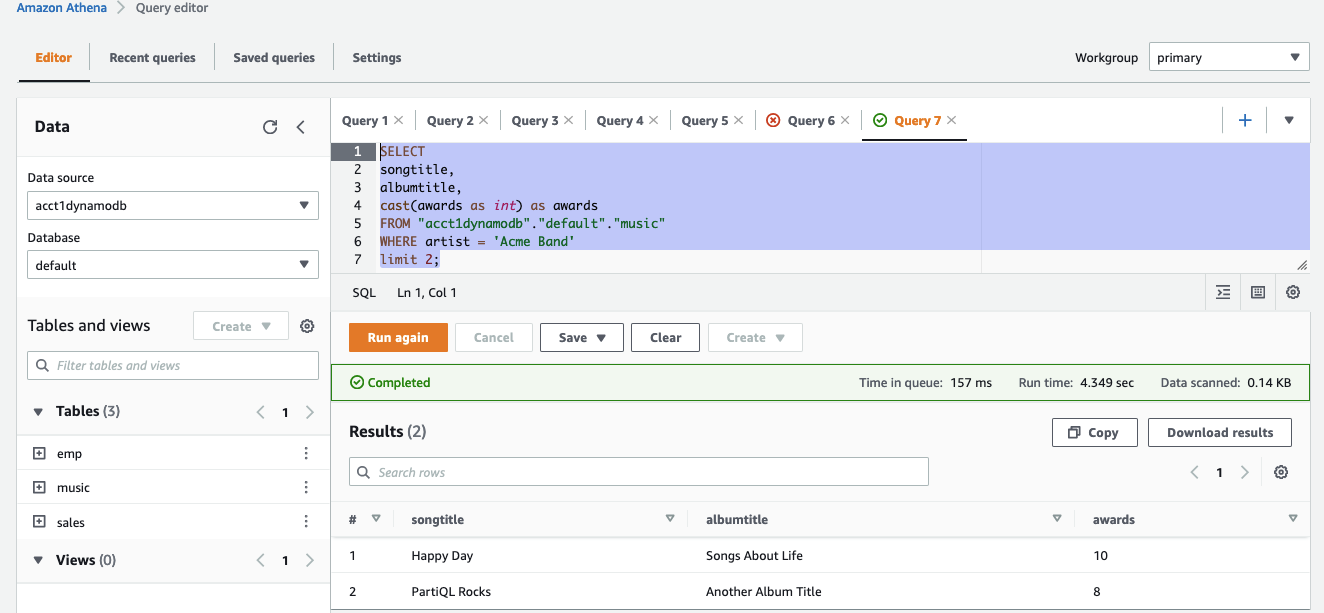
- 在 Athena Quer y 编辑器 中运行以下 SQL, ;
-
验证雅典娜联盟是否正常运行。
设置 Athena 跨账户联合
在账户 A 中:为跨账户设置 IAM 权限
- 以管理员身份登录账户 A。
- 在(Lambda 函数的)S3 泄漏存储桶上,向账户 B 的 IAM 用户分析师授予 getObject 和 ListBucket 权限。
注意 :将账户 b-ID 替换为要与之共享 DynamoDB 表的实际 亚马逊云科技 跨账户 ID。使用账户 A 中的实际 S3 存储桶替换溢出存储桶。
-
向 Accou
nt-B 的 IAM 用户分析师授予 Lambda 函数 acct1dynamodb 上的 I nvoke
Function。
注意 :将 Account-a-ID 替换为您有 DynamoDB 表的实际 亚马逊云科技 账户 ID。将账户 B-ID 替换为要与之共享 DynamoDB 表的实际 亚马逊云科技 跨账户 ID。
-
前往 Lambda 函数 acct1dynamodb 。选择 “ 配置和权限” 。
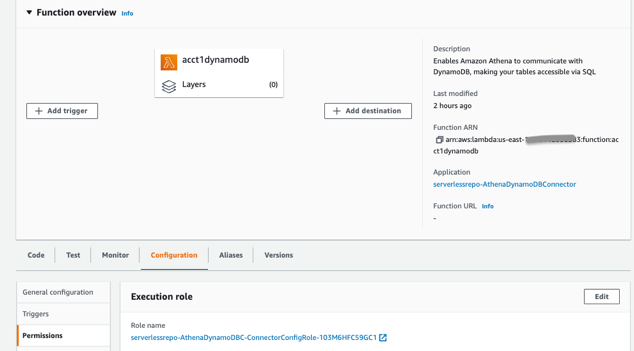
- 转到 基于资源的策略 和 添加权限 。
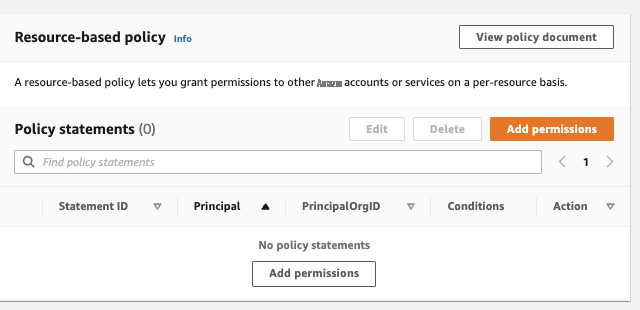
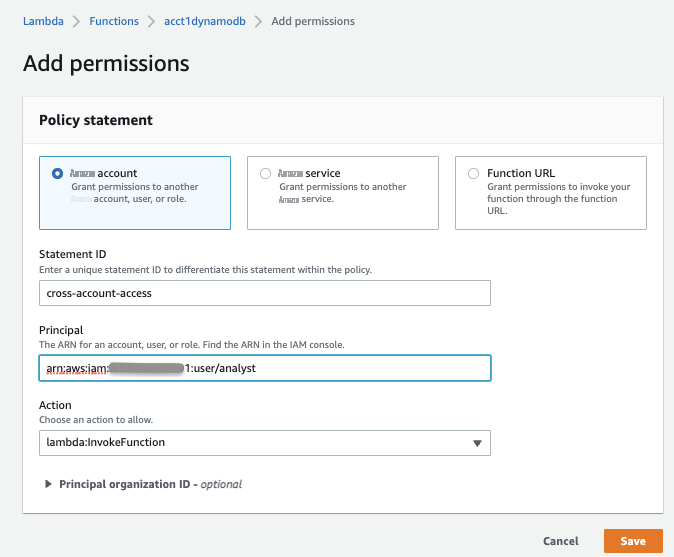
保存上述权限时,可以在 Lambda 函数的 基于资源 的策略 中的策略 声明 下 看到它们。
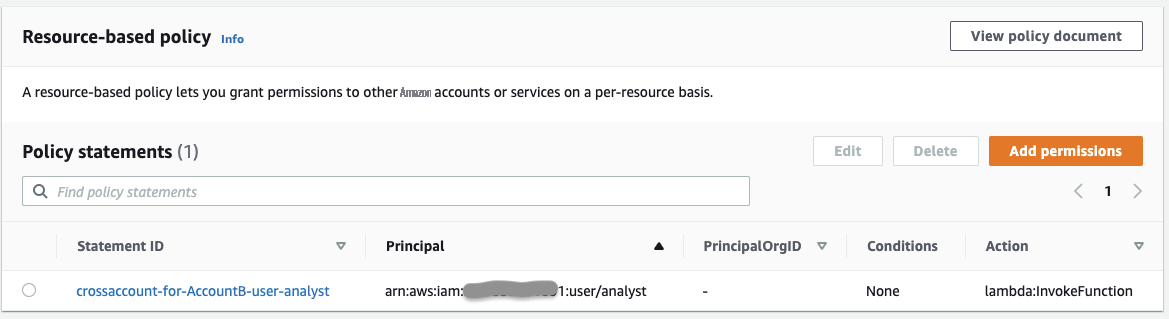
在账户 B 中:为跨账户设置 IAM 权限
- 以管理员身份登录 亚马逊云科技 账户 B。
-
创建 名为 A
thenacrossAccountFederated-Account-a-ID 的担任。向角色添加以下 内联策略 。IAM 角色 供账户 A
注意: 将账户 b-ID 替换为要与之共享 DynamoDB 表的实际 亚马逊云科技 跨账户 ID。
-
授予 IAM 用户分析师调用账户 A 的 Lambda 函数
acct1dymanodb 的权限
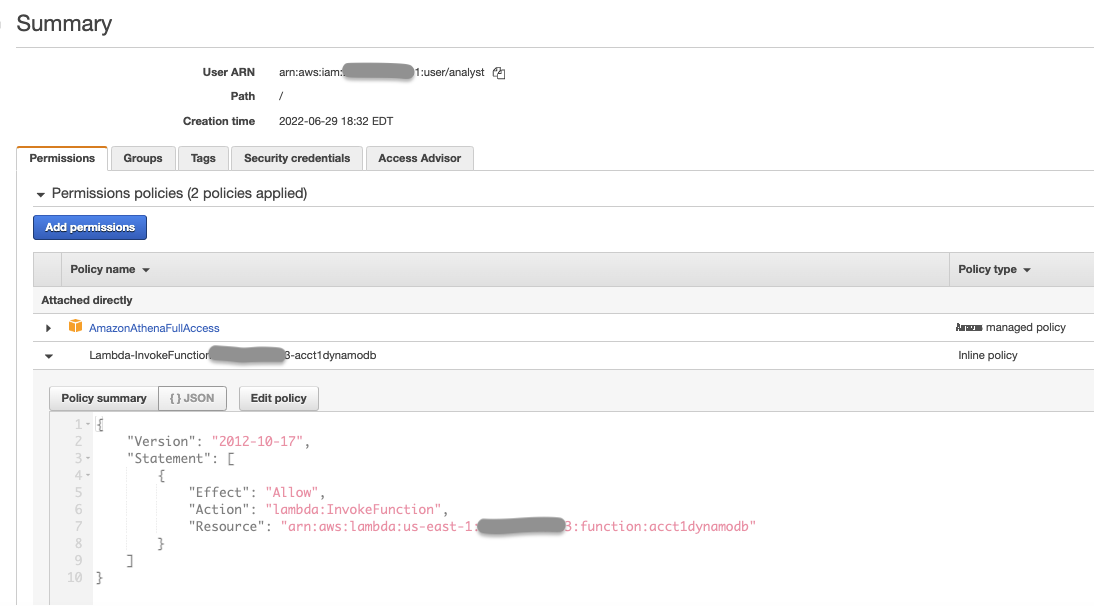
注意: 将 Account-a-ID 替换为您有 DynamoDB 表的实际 亚马逊云科技 账户 ID。
与 Account-B 共享 Athena 数据源
权限到位后,您将账户(账户 A)中的数据连接器与其他账户(账户 B)共享。账户 A 保留对连接器的完全控制权和所有权。当账户 A 对连接器进行配置更改时,更新的配置将应用于账户 B 中的共享连接器。
- 以管理员身份登录账户 A。
-
在 Athena 上,转到
数据源
,选择要共享的数据源
acct1dynamodb。转到右 上角的 “共享 ” 选项。
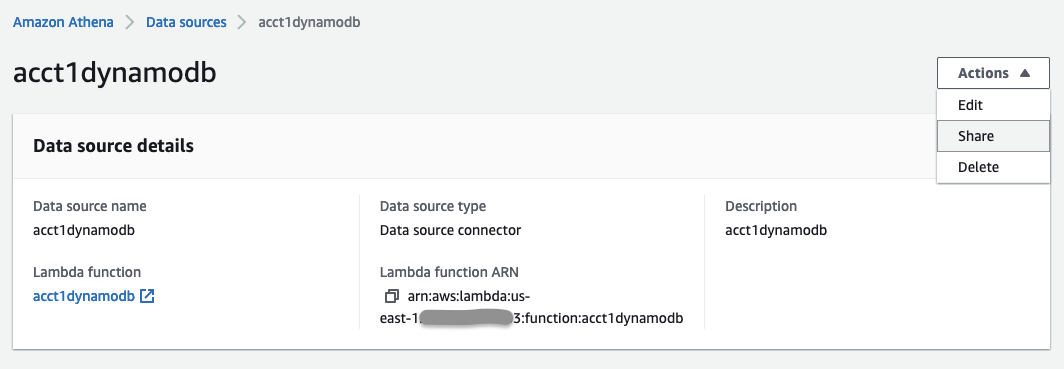
- 在 账户 ID 中 ,输入账户 b-ID 以与账户 B 共享您的数据源,然后点击共享。
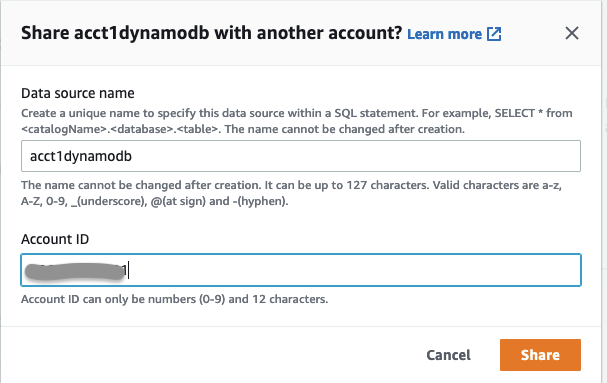

测试 Athena 跨账户联合查询:从 Account-B 访问共享数据源
- 以 IAM 用户分析师身份登录账户 B。
-
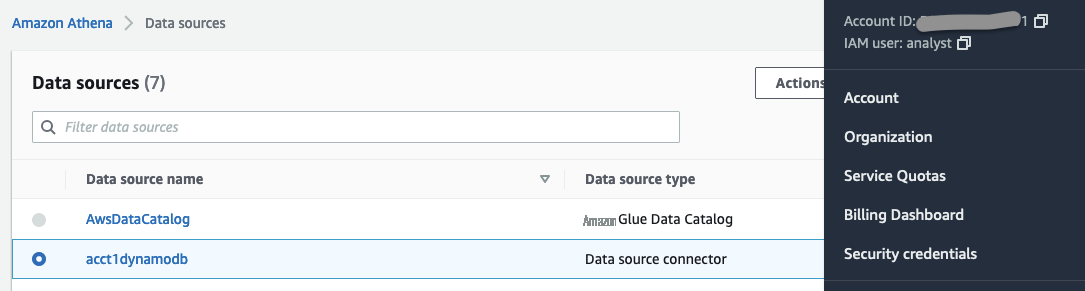
在 Athena 中,转到
数据源
。你会看到数据源
acct1dynamodb。
-
转到
查询编辑器
。从下拉列表中选择
数据源
acct1dynamodb。

- 您将看到共享数据源中的所有表。

- 在 Athena 查询 编辑器中运行以下 SQL

- 雅典娜跨账户联合成功了!这验证了账户 B 中的用户分析师可以看到账户 A 的 DynamoDB 表的数据。
清理
为避免将来产生费用,请删除为此演示预置的以下资源:
- 亚马逊云科技 Lambda 中使用的 S3 泄漏存储桶
- 用于数据源连接器的 Lambda 函数
- 示例 DynamoDB 表
结论
在这篇文章中,我们看到了如何使用 Athena Federated Query 访问跨账户 DynamoDB 表来就地查询数据。
作者简介

*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。