我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
通过 亚马逊云科技 PrivateLink 为亚马逊 S3 引入私有 DNS 支持
当本地应用程序使用云存储时,合规性要求通常要求使用私有连接。为了满足这些要求,客户 使用
为了帮助简化私有连接的 DNS 配置,Amazon S3
在这篇博客文章中,我们演示了如何利用私有 DNS 使用 亚马逊云科技 PrivateLink 访问 Amazon S3。我们还将讨论各种场景的配置选项,以及如何验证您的客户端是否通过网关 VPC 终端节点和接口 VPC 终端节点连接到 Amazon S3。
亚马逊 S3 的 VPC 端点
您可以使用两种类型的
网关 VPC 终端节点提供与 Amazon S3 和 DynamoDB 的可靠连接,无需为 VPC 安装互联网网关或 NAT 设备。只需在 亚马逊云科技 管理控制台中单击几下即可设置网关 VPC 终端节点,并使用您的 VPC 路由表通过 亚马逊云科技 网络将来自 VPC 内客户端的请求路由到 S3 或 DynamoDB 的公有 IP。网关 VPC 终端节点不收取额外费用,仅支持从本地资源到创建网关终端节点的相应 VPC 的连接。
接口 VPC 终端节点 使用 亚马逊云科技 PrivateLink 为
访问 S3 的最具成本效益的方法是尽可能使用网关 VPC 终端节点(例如,从该地区的 EC2 实例),并使用来自其他位置(例如本地)的 Interface VPC 终端节点。
使用私有 DNS 名称访问亚马逊 S3 接口终端节点
图 1
显示了一个混合网络设置,在该设置中,您可以通过 亚马逊云科技 Di
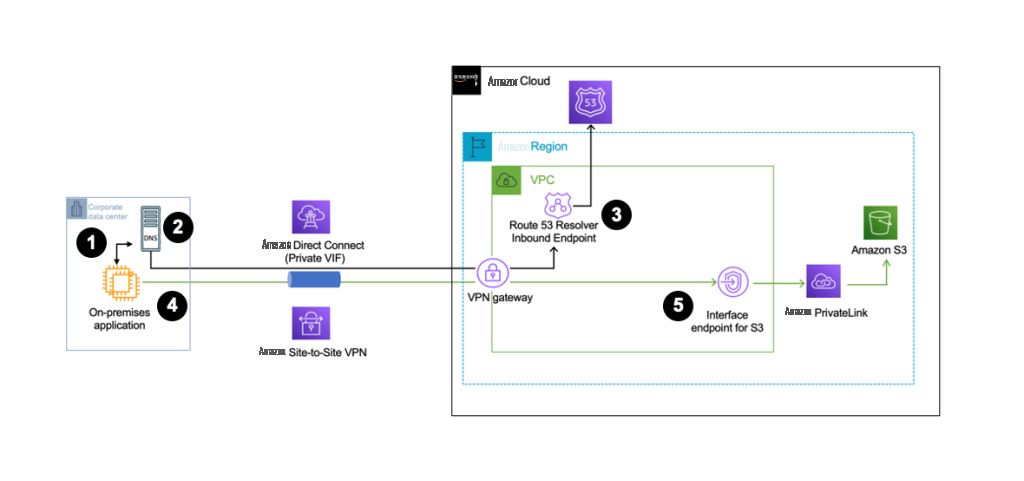
图 1:通过 Direct Connect 或 “点对点 VPN” 从本地进行连接时的设置
当您 为 S3 接口 VPC 终端节点启用
-
区域存储桶(例如,s3.
.amazonaws.com) -
控制(例如,s3 控制。
.amazonaws.com) -
接入点(例如,s3 接入点。
.amazonaws.com)
这使您能够使用 亚马逊云科技 与 S3 的私有网络连接,同时向服务的区域、控制或接入点终端节点发出请求。有关更多信息,请参阅适用于 Amazon
图表演练
- 本地客户端启动针对区域 S3 存储桶的 DNS 查询。
- 本地 DNS 服务器通过点对点 VPN 或 DX 连接将此查询转发到与具有 S3 接口 VPC 终端节点的同一 VPC 关联的相应 Route 53 解析器入站终端节点。
- Route 53 解析器终端节点将此查询转发到由 亚马逊云科技 管理的 Route 53 托管区域,该区域在 DNS 响应中返回 S3 接口 VPC 终端节点的 IP 地址。
- 然后,本地客户端启动与 S3 接口 VPC 终端节点的连接。
- S3 接口终端节点通过 亚马逊云科技 PrivateLink 将客户查询转发到客户查询中指定的 S3 存储桶。
新增- 仅为入站端点 启用私有 DNS
许多客户在本地和 亚马逊云科技 区域都有应用程序,两者都在同一 VPC 中运行。这些客户告诉我们,他们想要一种简便的方法,通过接口终端节点路由来自本地的流量,通过网关终端节点路由来自 亚马逊云科技 内部的流量。为了解决这个问题,
要解决此问题,请在 VPC 中创建网关终端节点。或者,您可以禁用 仅对入站端点 启用私有 DNS , 并将所有流量路由到接口终端节点。
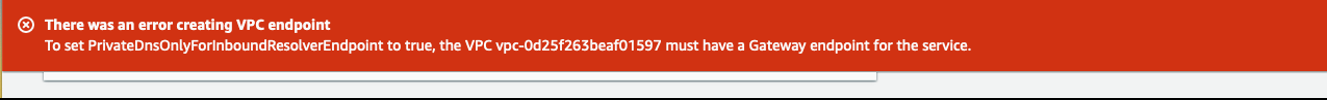
图 2:启用 PrivateDNSonlyforinboundPoint 时网关端点不存在时出现错误
先决条件
在开始之前,请确保满足以下先决条件:
-
在您希望通过
VPC 终端节点连接的 S3 存储桶所在的同一区域创建 VPC 。 确保已将属性 enablednshostNames 和 enablednsS upport 设置为真。 -
创建带有私有虚拟接口 (VIF) 的
亚马逊云科技 Direct Connect 连接 或 AWS 站点到站点 VPN 连接,以建立与公司数据中心的连接。 -
在步骤 1 中创建的同一
VPC 中为 S3 创建 网关 VPC 终端节点 ,以使用 “ 仅 启用私有 DNS” 入站终端节点 。
为 Amazon S3 创建接口 VPC 终端节点并启用私有 DNS 选项
- 要为 Amazon S3 创建接口 VPC 终端节点,请先导航到 VPC 控制台,选择 终端节点 ,然后选择 创建终端节点 。
- 对于 服务类别 ,选择 亚马逊云科技 服务 。然后,通过在搜索框中输入 S3 来筛选服务名称。对于 服务名称 ,将服务选择为 “S3”,对于 类型 ,请确保它显示 接口 ( 图 3a )。
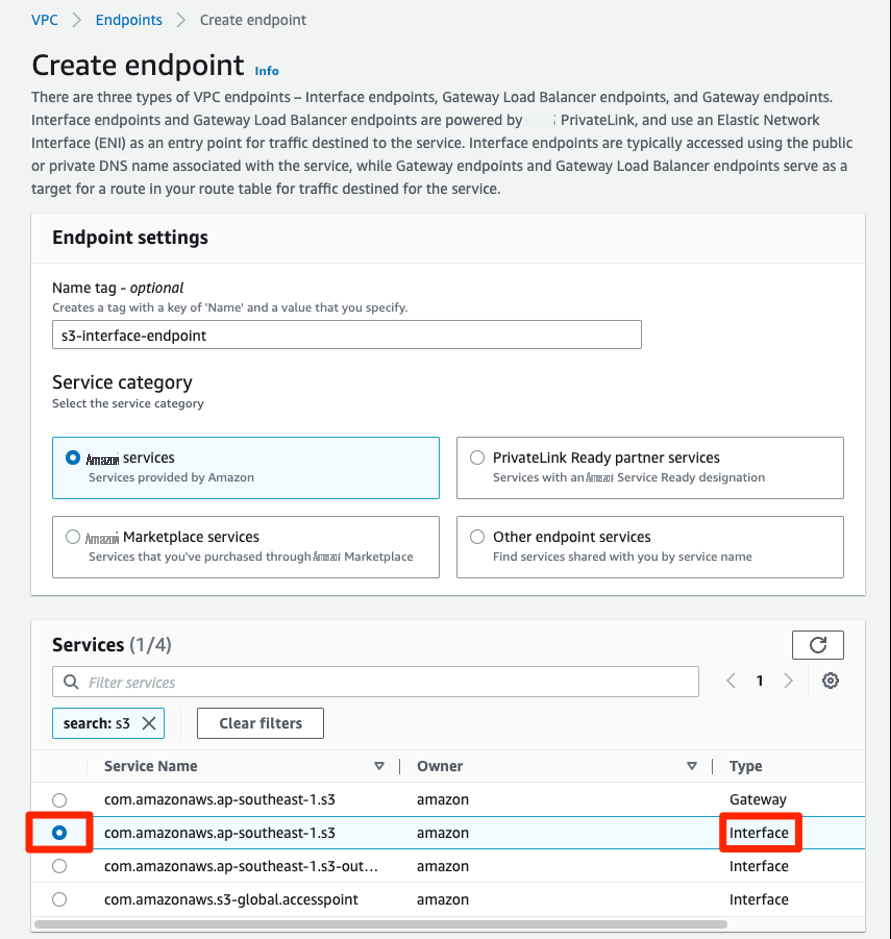
图 3a:为 S3 创建接口终端节点
- 为每个 VPC、所需的可用区域和子网选择,然后选择相应的安全组。这应该允许通过端口 443 来自您的网络的流量。
- 在 “ 其他设置” 下 ,选择 为您的接口终端节点 启用 DNS 名称 。默认情况下,它将选择 “ 仅对入站终端节点 启用私有 DNS ”, 以使源自您的 VPC 内部的流量流经网关 VPC 终端节点,而源自本地的流量流经接口 VPC 终端节点。
- 选择 创建端点 。我们在以下屏幕截图中显示了这一点( 图 3b ):
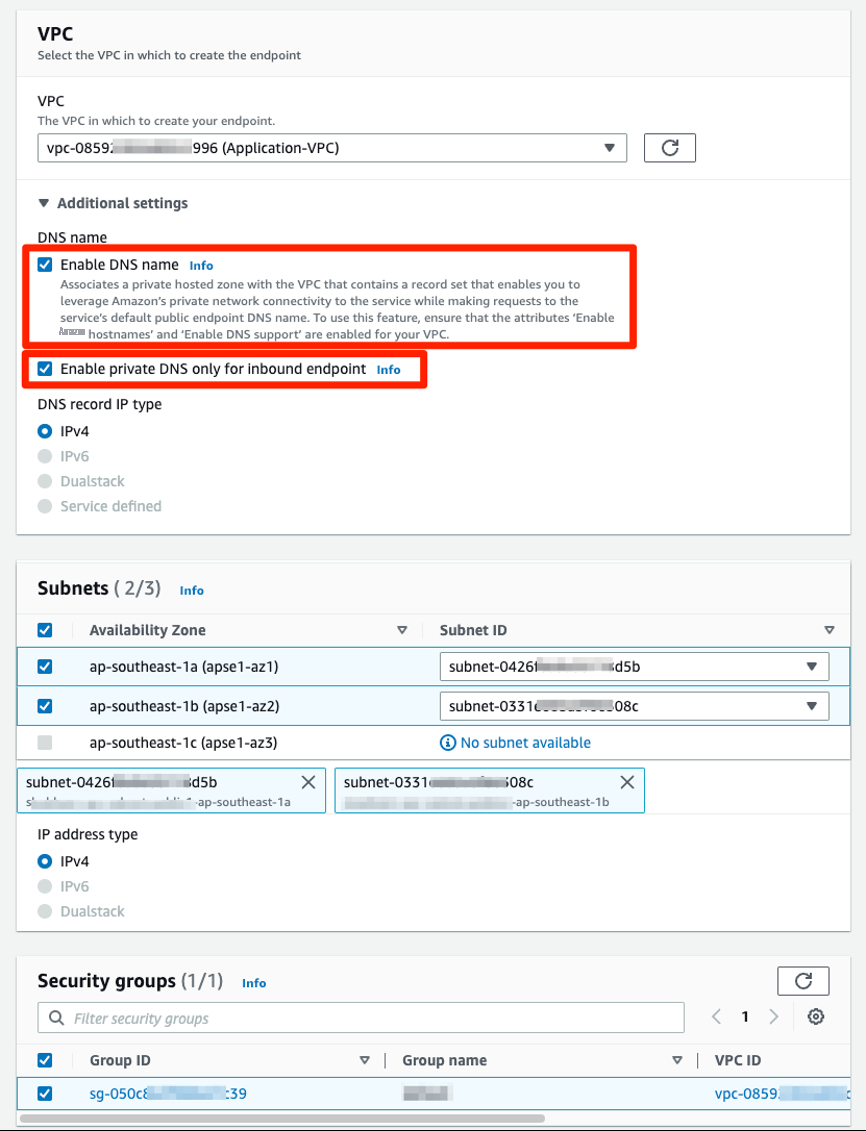
图 3b:在 VPC 控制台中创建接口 VPC 终端节点时选择私有 DNS 选项
在创建端点 时,需要花几分钟时间才能完成各种
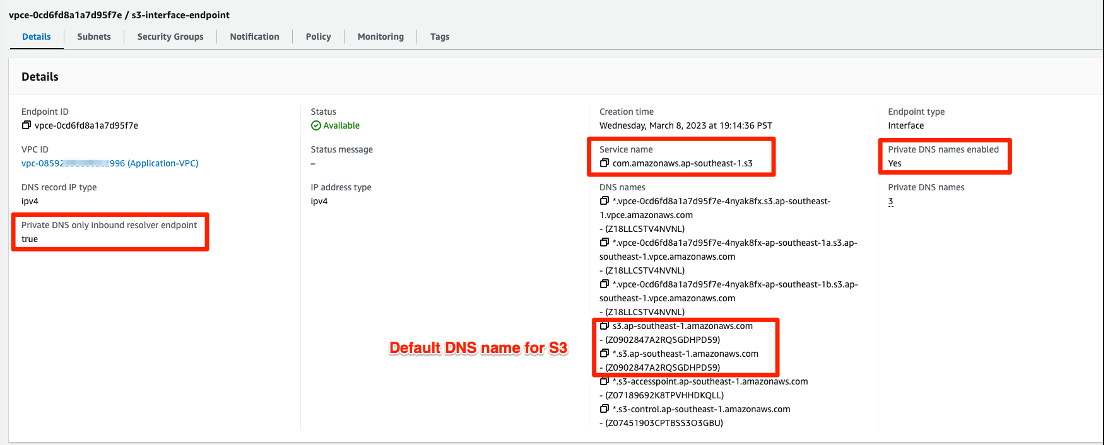
图 4a:接口 VPC 终端节点的详细信息
选择 Subnet s 以查看接口端点的位置以及每个子网中端点网络接口的 ID。在下面的屏幕截图( 图 4b )中,VPC 中终端节点网络接口的私有 IP 地址是 10.0.4.122 和 10.0.23.155。
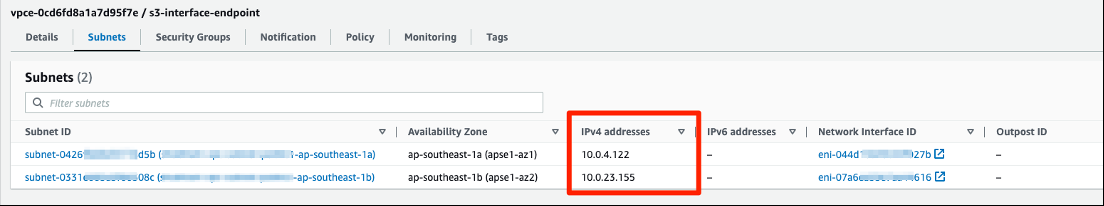
图 4b:您的接口 VPC 终端节点的子网信息
私有 DNS 选项的场景
让我们了解一下影响客户端使用适用于 Amazon S3 的网关和接口 VPC 终端节点从 VPC 和本地托管的应用程序与 Amazon S3 的连接的 DNS 选项的各种组合:
场景 1 : 没有 私 有 DNS 选项
在此配置中,来自创建网关终端节点的 VPC 内客户端的流量可以连接到 S3 区域终端节点。
当您想要灵活地在自己的私有托管区域中管理私有 DNS 名称时,此选项非常有用。
VPC 中使用网关终端节点的客户端:
VPC 中或本地使用端点专用 DNS 名称的客户端:
前面的输出显示,VPC 内部的客户端解析为 S3 服务终端节点的公有 IP 地址,而企业数据中心中的客户端解析为 Amazon S3 接口 VPC 终端节点 ENI IP 地址。
场景 2 : 使用私有 DNS
在此配置中,VPC 内和本地流量均通过 S3 的接口 VPC 终端节点流动。当您想要简化架构以仅使用一种终端节点时,此选项很有用,因为它简化了 DNS 管理。但是,这不是一个经济高效的解决方案,因为现在从 VPC 中的资源到 S3 的流量也会产生与 S3 接口 VPC 终端节点相关的数据传输费用。VPC 如 图 5 所示 ,绿色和蓝色表示流量从 VPC 和本地环境中的 EC2 实例通过 S3 的接口 VPC 终端节点流动。
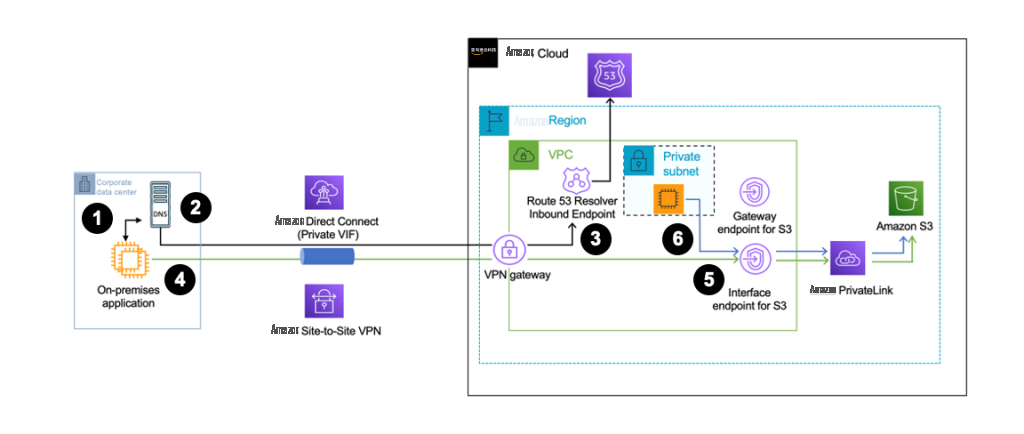
图 5:启用私有 DNS 并禁用仅对入站端点启用私有 DNS
图表演练
所有步骤 1 到 5 保持不变,如 图 1 所示 。但是,现在只有 VPC 内 启用 私有 DNS 的 客户端以及本地客户端通过 S3 接口 VPC 终端节点连接到 Amazon S3。
VPC 内的客户端:
本地应用程序内部的客户端:
前面的输出显示,VPC 内部和本地的客户端都解析为接口 Amazon S3 的 VPC 终端节点 ENI IP 地址。
场景 3: 仅为入站解析器端点 使用 私有 D NS
在此配置中,来自 VPC 内应用程序的流量流经网关 VPC 终端节点,而本地流量则流经接口 S3 的 VPC 终端节点。此选项为从 VPC 和本地应用程序访问 S3 提供了经济实惠的网络设计。选择此配置时,您需要在您的 VPC 中维护网关 VPC 终端节点。这是为了让您的流量始终保持在 亚马逊云科技 私有网络上。这消除了在没有网关终端节点的情况下,您的 VPC 内流量无意中通过互联网网关或者在没有互联网网关时被丢弃的可能性。因此,如果您运行应用程序的 VPC 中不存在网关 VPC 终端节点,它将阻止您选择 “
仅为入站终端节点 启用私有 DNS
” 选项
。如果您想将现有接口终端节点更新
为仅对入站终端节点 启用私有 DNS
,则必须确认您的 VPC 具有适用于 S3 的网关 VPC 终端节点。有关网关 VPC 终端节点和管理私有 DNS 名称的更多信息,请 分别参阅 亚马逊云科技 PrivateLink 指南中的
图 6 显示了从 VPC 内 EC2 实例流经网关 VPC 终端节点的流量的蓝色路径,而绿色路径显示了使用接口 VPC 终端节点从本地流向 S3 的流量。
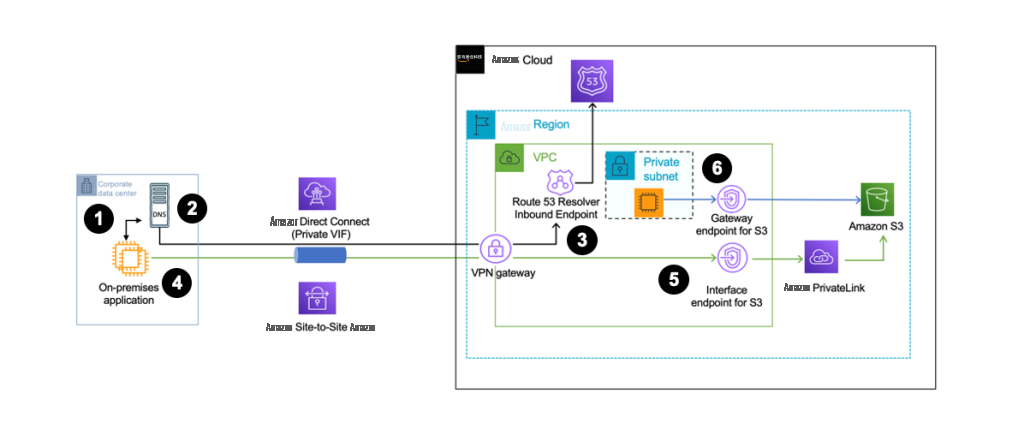
图 6:启用私有 DNS 并仅为入站端点启用私有 DNS
图表演练
所有步骤 1 到 5 与 图 1 相同 。但是,现在 私有 DNS 和 “ 仅对入站终端节点 启用私有 DNS ”,VPC 内的客户端通过 S3 的网关 VPC 终端节点连接到 Amazon S3,而本地客户端则通过 S3 的 VPC 接口 VPC 终端节点连接到 Amazon S3。
VPC 中使用网关终端节点的客户端:
使用接口端点的本地客户端:
当私有 DNS 和 仅为入站终端节点 启用私 有 DNS 时,您无法删除网关 VPC 终端节点 。如果你尝试这样做,它会引发以下错误:
“当服务的接口端点将 privatednsonlyforinboundResolverendPoint 设置为 true 时,无法删除网关端点。”
在这种情况下,如果要删除网关 VPC 终端节点,则需要修改接口 VPC 终端节点并取消选择 “ 仅为入站终端节点 启用私有 DNS” 选项。
结论
在这篇博客文章中,我们讨论了使用私有 DNS 作为 Amazon S3 接口 VPC 终端节点在不修改本地应用程序的情况下访问 Amazon S3。我们介绍了使用 “
仅为入站端点 启用私有 DNS
” 选项来优化 S3 的网络路径。这些选项使您能够利用成本最低的私有网络路径,而无需对客户端进行代码或配置更改。
有关适用于 Amazon S3 的 亚马逊云科技 PrivateLink 的更多信息,您可以参考以下博客:
-
使用 亚马逊云科技 PrivateLink 安全混合访问亚马逊 S3 -
为亚马逊 S3 选择您的 VPC 终端节点策略 -
亚马逊云科技 合作伙伴使用 亚马逊云科技 PrivateLink 私密连接到 Amazon S3
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。