我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
使用 亚马逊云科技 IoT Device Defender 识别配置错误的物联网策略
简介
我们很高兴地宣布一项新的
背景
在某些情况下,由于物联网策略通配符和 MQTT 通配符之间的混淆,客户可能会错误地配置物联网策略。如果客户以某种方式配置物联网策略,则可以超额订阅设备以接收主题数据,而设备本应被明确拒绝订阅。
在这篇博客中,我们将讨论两种类型的错误配置,以及如何使用 亚马逊云科技 IoT Device Defender 审计来识别和修复 IoT 策略中这些潜在的错误配置。
在 MQTT 和 亚马逊云科技 IoT Core 策略中使用通配符
MQTT 和 亚马逊云科技 IoT Core 策略具有不同的通配符,您应在仔细考虑后选择它们。在 MQTT 中,在 MQTT 主题过滤器中使用通配符 “+” 和 “#” 来订阅多个主题名称。字符 “+” 代表单个 MQTT 主题关卡,“#” 代表多个 MQTT 主题关卡。亚马逊云科技 IoT Core 策略使用 “*” 和 “?”作为通配符并遵守 IAM 策略的惯例。在政策文件中,“*” 代表字符和问号 “?” 的任意组合代表任何单个字符。在政策文件中,MQTT 通配符 “+” 和 “#” 被视为没有特殊含义的字符。要描述策略的资源属性中的多个主题名称和主题筛选器,请使用 “*” 和 “?”使用通配符代替 MQTT 通配符。
在选择要在政策文档中使用的通配符时,请考虑到 “*” 字符并不局限于单个主题级别,因为 “+” 字符位于 MQTT 主题筛选器中。为了帮助将通配符规范限制为单个 MQTT 主题过滤器级别,可以考虑使用多个 '?'人物。有关
有两种类型的错误配置:
类型 1: 当客户希望设备接收整个主题空间 “ building/*” 的消息,但不希望接收与 “building/control_room/* ” 相关的特定子主题的消息时。
在此示例中,主题过滤器旨在拒绝访问,但使用通配符会导致允许访问。在包含允许语句中带有通配符的主题过滤器和具有允许资源子集的拒绝语句的策略中,可以通过订阅通配符来访问拒绝主题消息。
{
效果:允许
操作:订阅
资源:/topicfilter/building/ *
效果:拒绝
操作:订阅
资源:/topicfilter/building/control_room/ #
效果:允许
操作:接收
资源:/主题/建筑物/ *
}
但是,当设备订阅 “b uilding/#” 时,它会收到来自 “building/ control_room/3” 的消息。
这是因为主题 “ building/#” mat ches 允许 “ building/* ”,授权设备的订阅操作。请注意,在应用程序代码的下方,“ building/# ” 匹配所有数据,并且由于设备已经订阅,它将接收所有匹配的主题数据。
当您在适用于 MQTT 客户端的 亚马逊云科技 IoT Core 策略中指定主题筛选条件时,MQTT 通配符 “+” 和 “#” 被视为文字字符串。它们的使用可能会导致意想不到的行为。
如何修复:
{
效果:允许
操作:订阅
资源:/topicfilter/building/ *
效果:拒绝
操作:订阅
资源:/topicfilter/building/control_room/ *
效果:拒绝
操作:接收
非资源:/topic/building/control_room/ *
}
完成此操作后,设备将接收在 topic/(例如 “ building/common_area”)下的任何主题上发布的消息,但是,设备不会收到在 “building/control_ room/ ”(例如 “ building/control_room/ 3”)下的任何主题上发布的任何消息
在某些合理的用例中,作者可能是这样做的,例如,允许维护人员进入特定的空间(例如 ' /building/control_room/3 ')。因此,在我们的 亚马逊云科技 IoT Device Defender 审计检查中,我们将其列为潜在的配置错误,由用户来决定,这是故意还是非故意的错误配置。
类型 2: 当客户希望设备接收整个主题空间 “ 建筑物/相机/*” 的消息时,但不希望接收涉及 control_room 的特定子主题的消息, 如 “建筑/ +/control_room”。在使用特定字符串替换通配符时,设备可能会避开 Deny 语句中的 MQTT 通配符。
{
效果:拒绝
操作:订阅
资源:/topicfilter/building/+/control_room
效果:允许
操作:订阅
资源:/topicfilter/building/camera/ *
}
所需的行为是拒绝设备访问 “ 建筑物/相机/控制室”,但允许访问 “建筑物/相机/ 住宅 1 ”。
但是,设备可以向主题 “/building/ +/control_room” 发送请求,并最终收到来自主题 “/building/camera/control_room ” 的消息。
如何修复:
{
效果:拒绝
操作:订阅
资源:/topicfilter/building/ */control_room
效果:允许
操作:订阅
资源:/topicfilter/building/camera/ *
效果:允许
操作:接收
资源:/主题/建筑物/相机/ *
效果:拒绝
操作:接收
资源:/topic/building/ */control_room
}
通过此修复,物联网策略将允许设备接收来自以下来源的消息:
/建筑物/相机/住宅 1
/建筑物/相机/住户2
/建筑物/相机/住宅 3
但不是来自
/building/camera1/控制室
/building/camera2/控制室
/building/any_camera/控制室
使用 亚马逊云科技 IoT Device Defender 审计检查来识别潜在的错误配置
在本节中,我们将介绍如何在 亚马逊云科技 IoT 控制台中针对前面描述的两种错误配置进行配置、运行和采取纠正措施。
在此示例中,我们在 亚马逊云科技 IoT 中输入了类型 1 和类型 2,如下所示:
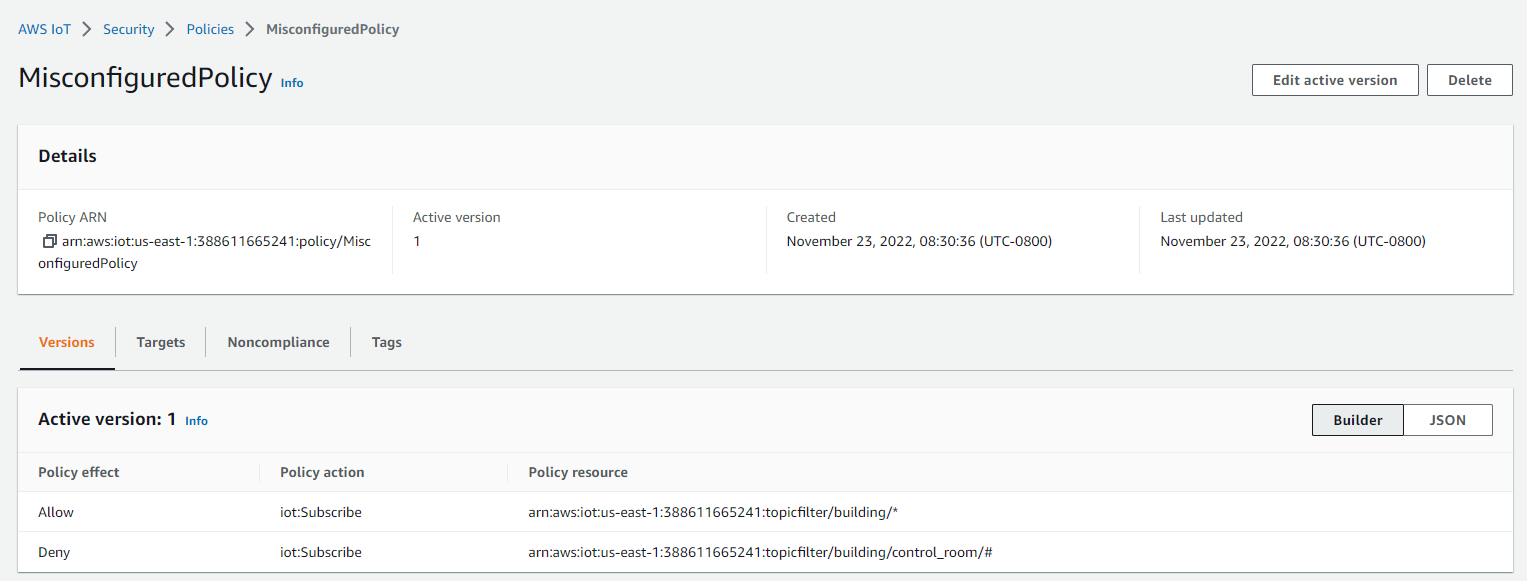
图 1:在 亚马逊云科技 IoT 中配置为 “配置不当策略” 的类型 1 策略
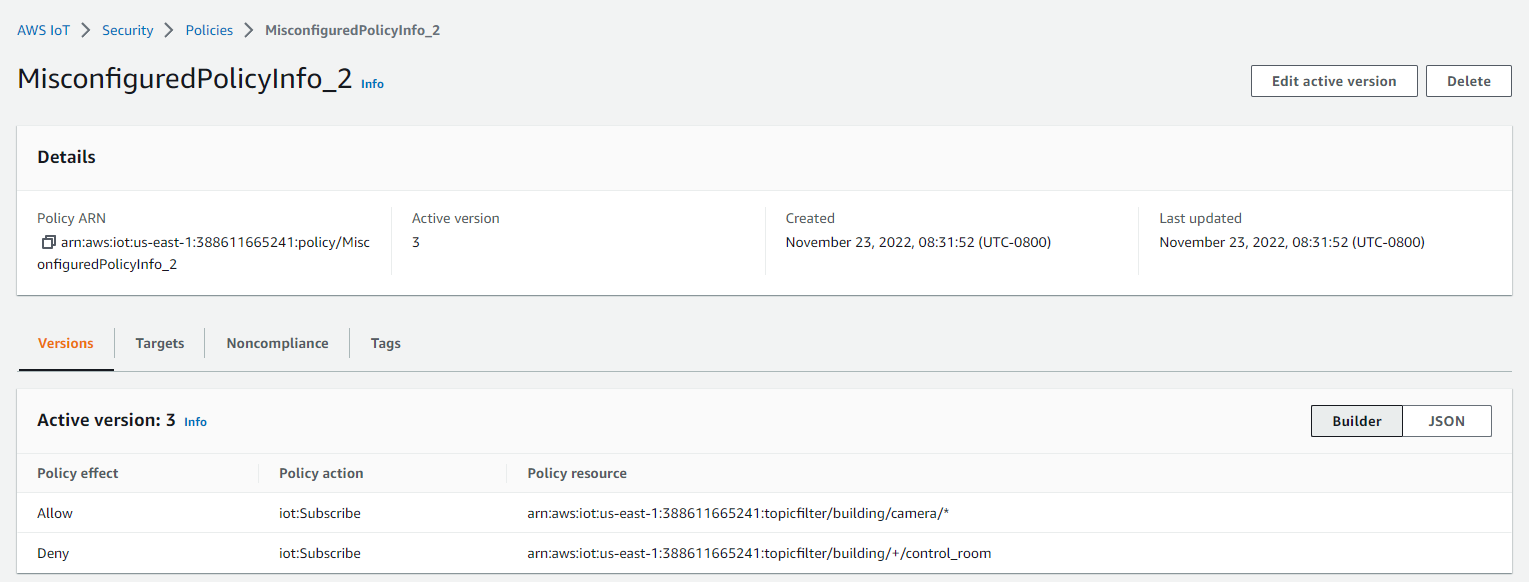
图 2:在 亚马逊云科技 IoT 中配置的名为 “misconfiguredPolicyInfo_2” 的类型 2 策略
然后,在我们运行新的 “物联网策略可能配置错误” 的审计检查后,当此检查发现可能配置错误的 亚马逊云科技 IoT 策略时,将返回以下原因代码:
a) 策略_包含_MQTT_WILDCARDS_IN_DENY_STATEMENT
b) TOPIC_FILTERS_INTENDED_TO_DENY_ALLOWED_使用通配符
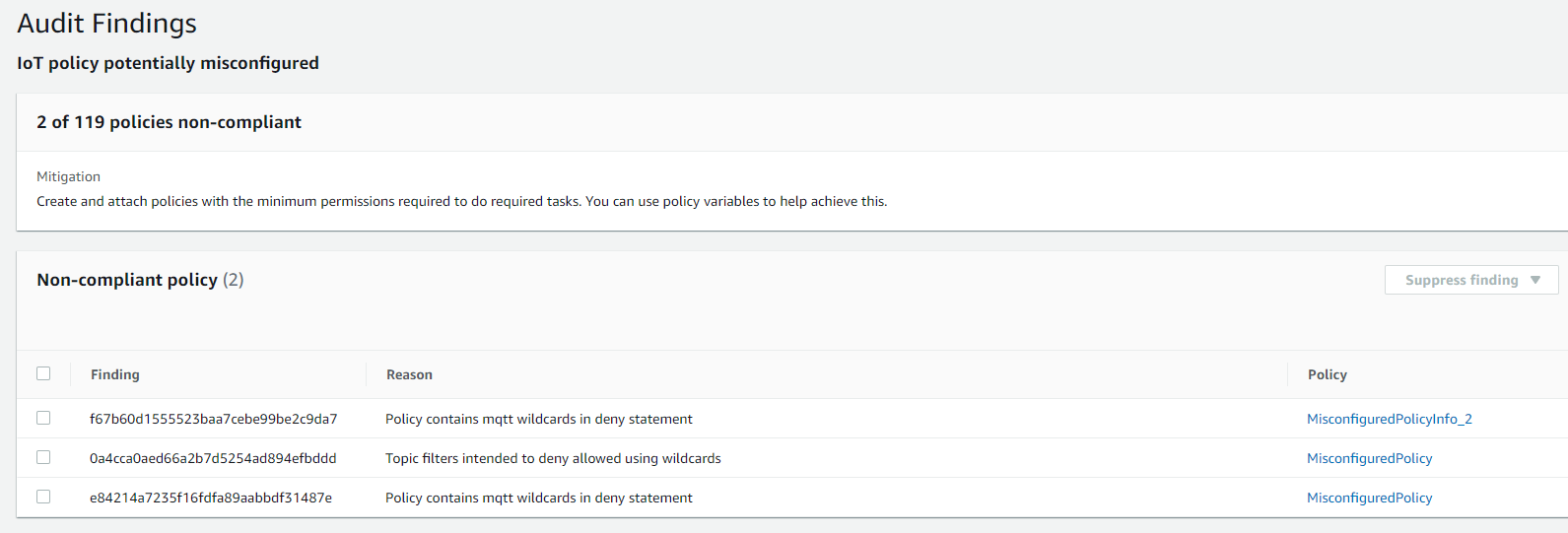
图 3:亚马逊云科技 IoT Device Defender “物联网策略可能配置错误” 审计检查的结果
亚马逊云科技 IoT Device Defender 的 “物联网策略可能配置错误” 检查会检查拒绝语句中是否有 MQTT 通配符(“+” 或 “#”)。在政策文件中,通配符被视为文字字符串,可能会使其过于宽松。
如何修复
此审计检查将可能存在误配置的策略标记为可能存在误报,因为可能存在误报。使用
您也可以按照以下步骤修复附加到事物、事物组或其他实体的任何不合规策略:
-
使用
createPolicyVer sion 创建新的、兼容的策略版本。将 setaSdefault 标志设置为 true。(这使得这个新版本适用于所有使用该策略的实体。) -
验证所有关联设备都能够连接到 亚马逊云科技 IoT Core。如果设备无法连接,请使用
setPolicyV ersion 将默认策略回滚 到先前版本,修改策略,然后重试。
结论
在这篇文章中,你已经了解了如何使用 亚马逊云科技 IoT Device Defender 审计来发现物联网策略中潜在的错误配置。“物联网策略可能配置错误” 审计功能可检查物联网策略中通配符的使用情况,并在出现潜在错误配置时提醒您。然后,您可以遵循安全建议,并在需要时采取纠正措施。这项新的审计检查使客户可以更轻松地减少物联网策略的错误配置,并帮助您改善物联网解决方案的安全状况。
如果您使用 亚马逊云科技 IoT Device Defender,则可以在 亚马逊云科技 IoT Device Defender 审计部分启用新的审计检查。如果您不熟悉 亚马逊云科技 IoT Device Defender,则可以在 亚马逊云科技 IoT 控制台中通过一键式流程来改善物联网设备队列的安全状况。有关更多信息,请参阅 亚马逊云科技 IoT Device Defender
作者
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。