我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
Devocean 如何使用亚马逊 Neptune 为云原生应用程序构建漏洞修复管理平台
在这篇文章中,我们将讨论
Devocean 是一家领先的软件即服务 (SaaS) 开发公司,为全球企业组织提供云原生应用程序漏洞修复管理和自动化解决方案。其统一平台解决方案为开发、基础设施安全和应用程序安全团队提供了单一事实来源,以实现对云资产及其关联风险的可见性和控制,从而弥合了他们之间的鸿沟。
Devocean 为其客户的云应用程序构建了虚拟蓝图,为他们提供了资产和风险如何关联以及架构偏移如何影响他们的实时可视化。
借助 Devocean,安全团队能够获得所需的背景信息,以确定风险优先级、减少噪音并与组织内的相应团队一起管理补救措施。
Devocean
Devocean 漏洞修复平台概述
下图说明了平台内的数据架构。
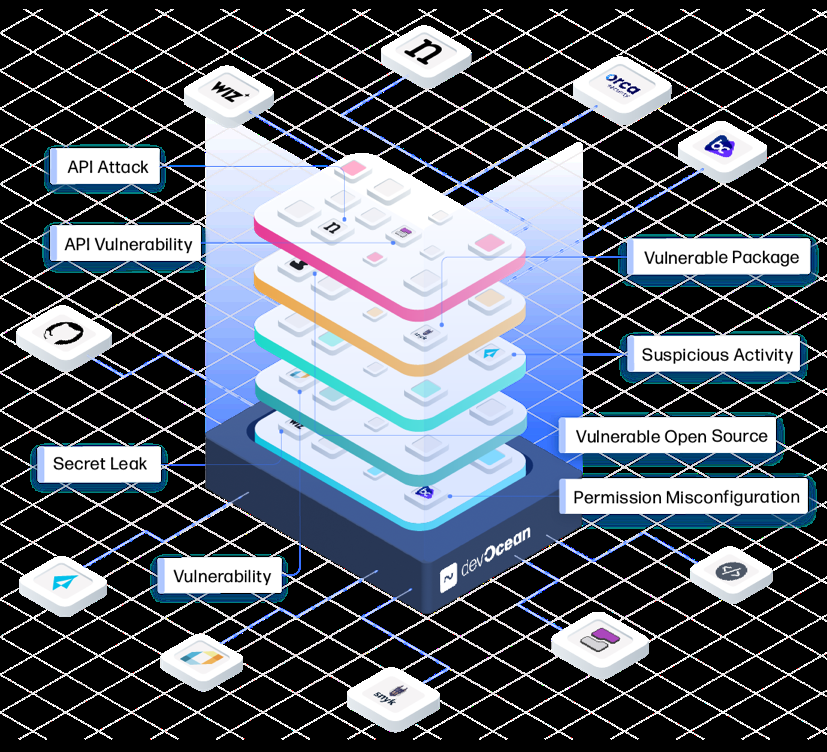
Devocean 平台使用 亚马逊云科技 无服务器微服务架构构构建。通过连接到客户云帐户并收集所有云资产及其配置和元数据来收集数据。
同时,该平台连接到客户连接的安全工具(例如CSPM、CWPP、CNAPP、代码漏洞扫描器、最低权限和其他 OSS 工具)并提取安全事件。
然后,管道将数据推送到海王星,在海王星中,智能聚类逻辑连接数据并为发现结果添加上下文。在这种背景下,Devocean提出了风险优先级建议。例如,安全工具可能会对特定的安全事件给予较高的评级,但Devocean认为其风险较低,因为该事件与测试环境中的资产有关。
Devocean 的智能集群还允许对不同工具报告的关联事件进行重复删除,同时识别根本原因事件,大大减少噪音量,减少解决单个问题所需的票证数量。
通过从数十万个不同的安全事件、工具和云资产中创建统一的安全画面,Devocean 为云原生应用程序提供管理和自动风险修复所需的上下文。
以下屏幕截图说明了 Devocean 用户界面。
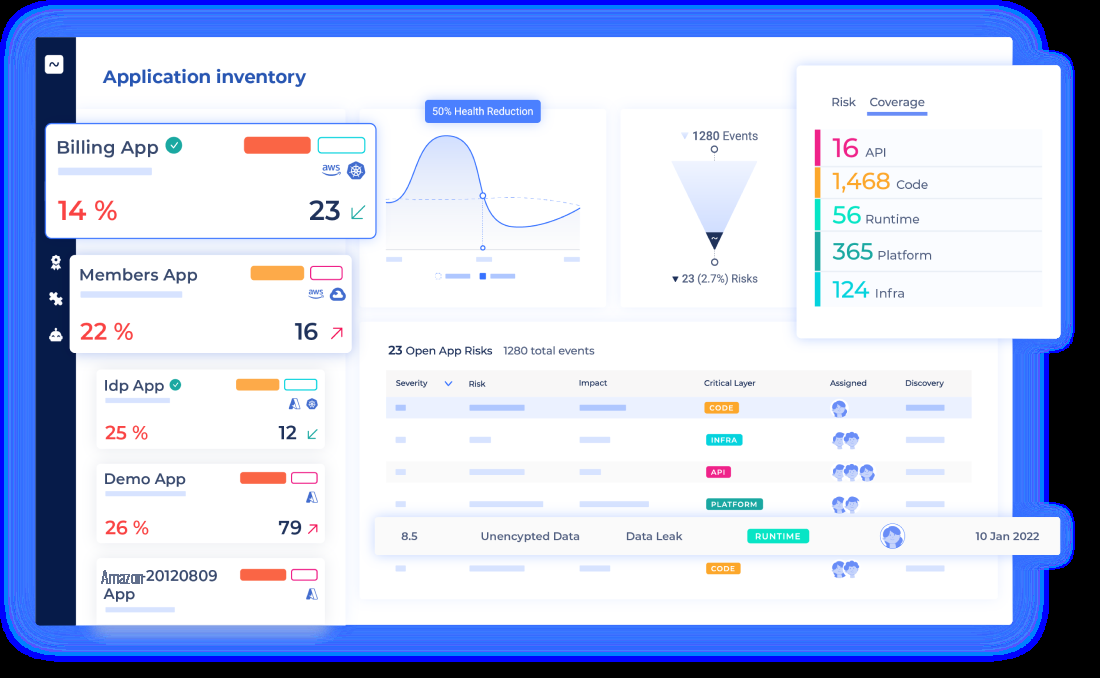
解决方案概述
Devocean 是一种无需代理的部署,可以在几分钟内将其部署到您的云端。在最初的入职阶段,它会连接到您的所有云帐户,并开始从您的所有资产中收集数据。之后,数据收集将持续进行,以维护云环境的蓝图始终处于最新状态。
这会生成大量需要存储的数据,以便将其聚集到应用程序和微服务中,从而使Devocean能够突出关系和使用情况,并生成由上下文驱动的有意义的见解。
在系统开发过程中,Devocean 团队检查了所需的数据访问模式。他们需要一个安全且易于扩展的高性能数据库,并且可以轻松集成到Devocean的无服务器架构中。当然,高水平的支持也至关重要。
很明显,图形数据库可以最有效地满足这些要求,在评估其选项之后,Devocean选择了Neptune作为运行其SecOps平台的图形数据库。
为什么是海王星?
Devocean 平台是由
作为一项托管服务,Neptune与其他构造Devocean后端的托管服务集成在一起,从而简化了内部服务通信。此外,在一个平台 (亚马逊云科技) 中管理所有数据库可以简化支持、调试和监控流程。
构建应用程序蓝图:将数据聚类到应用程序中
用于验证这一点的一个示例是检查应用程序资源是否构造了一个循环子图,该循环子图在其资源之间具有很高的内聚力,但与其他子图的耦合度低。如果算法找到可以回答此特定规则的应用程序,则它是一个新的应用程序。
以下屏幕截图显示了一个账户(在灰色圆圈中),里面有三个应用程序。每个应用程序都包含资产及其连接。我们的平台已将资产分组到应用程序中,因为这些资产是相互关联的。根据通信、日志、策略等在资产之间创建连接。
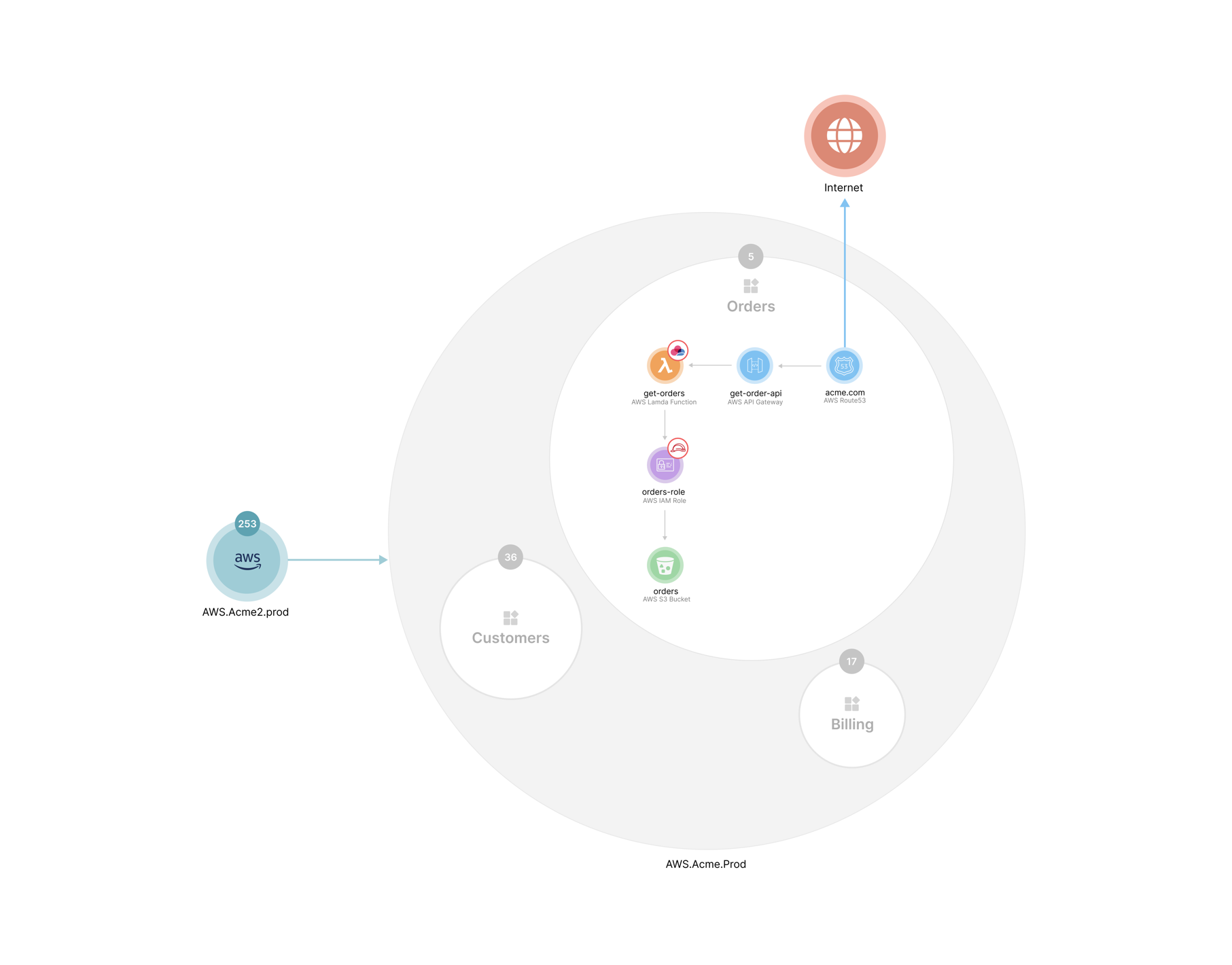
使用 Neptune 批量加载器及其快速查询引擎,集群过程需要几分钟。集群过程结束后,使用 NLP 来定义应用程序名称。
更快地生成风险意味着更快地修复风险
Devocean 平台中的风险是根据
风险可以由规则生成,例如:如果存在安全事件 X 的 API 网关连接到数据库 Z 中存储数据的
为了产生这种风险,Devocean 会扫描从客户那里检索到的所有数据。扫描图形数据库中资源之间的关系比在任何其他数据库中扫描都容易得多。
利用 Neptune,Devocean 创建了一个模型,该模型将图表上的元数据和使用情况存储在查询所需的属性中,并将不可搜索的元数据存储在另一个数据库中。这样,他们可以确保他们只将数据加载到要查询的图表中。
例如,该代码的编写方式是,资源的每个字段都可以存储在图表中,除非它不可搜索,在这种情况下,它将存储在键值存储中。
IAC 部署、租户配置和灾难恢复
Devocean 的后端服务及其依赖项使用 IaC 进行配置并部署到 Devocean 的 亚马逊云科技 后端账户。也可以配置部署帐户和区域。
Neptune 使 Devocean 的 iaC 部署、租户配置和灾难恢复变得快速而轻松。作为一项托管服务,Neptune 可与 Devocean 的无服务器生态系统无缝集成,可由 亚马逊云科技 CDK 部署,从而确保 DevoCean 可以快速部署到其他地区或账户。
快速提供租户对于快速吸引新客户至关重要。Devocean 使用 亚马逊云科技 CDK 进行租户配置流程。
借助 Neptune 租户策略及其基于后端角色的访问控制,他们可以确保租户在 Neptune 集群中分离。
作为对此的改进,Devocean目前正在努力利用
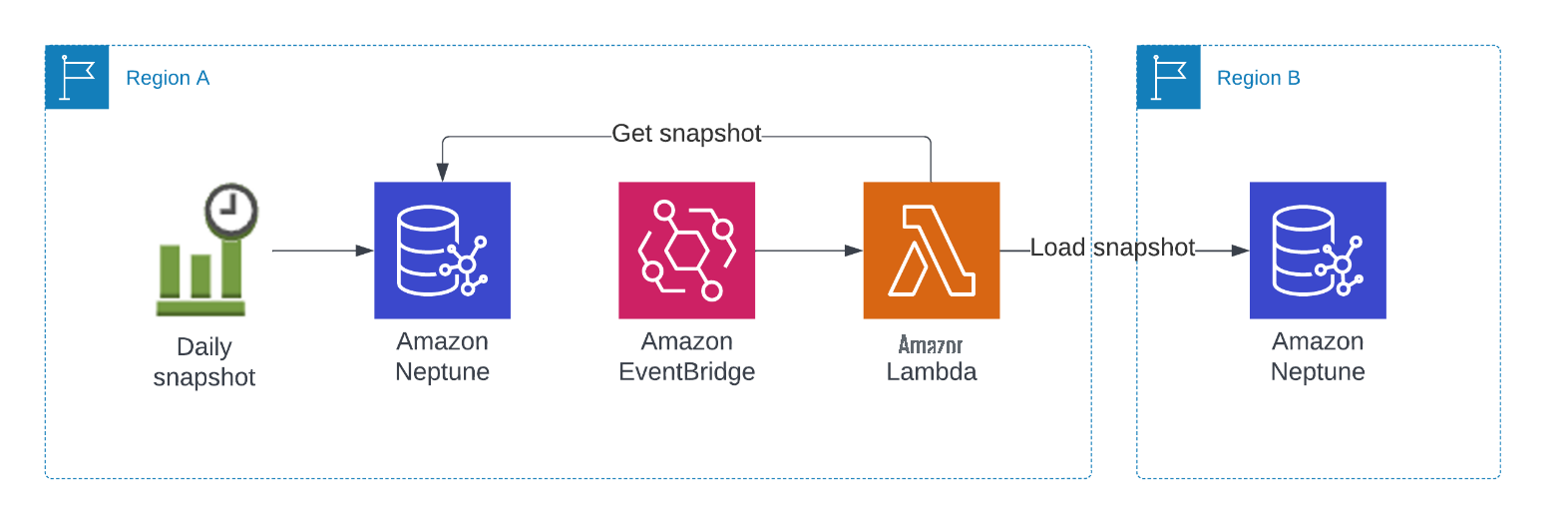
帮助Devocean选择海王星的另一项关键功能是灾难恢复,这要归功于他们的iAC策略和海王星的能力。
例如,如果发生灾难,Devocean 需要在不同的地区重新创建客户的账户。此外,在灾难恢复方面,除了快速重新部署之外,海王星还有其他好处。它还有助于确保不会丢失任何数据。Devocean 使用 Neptune 快照并在每个客户收集过程中备份数据,以确保不会丢失任何数据。重新创建环境时,系统会检查最近是否有快照,如果有,则将它们加载到 Neptune 中。几分钟之内,客户的账户就充满了最新数据。
下图说明了这种架构。
Devocean 的后续步骤
摘要
在这篇文章中,我们探讨了Devocean如何使用Neptune为云原生应用程序构建修复平台,通过丰富的背景将云资产与风险关联起来。对于组织而言,获取云原生应用程序风险的可见性和背景信息不再是一个复杂的手动过程。借助 Devocean,安全团队可以在单个平台中管理来自各个孤立工具的合并安全警报并确定其优先级。
借助此产品,Devocean 正在为其客户简化云原生风险管理和自动化。由于整个解决方案架构都在 亚马逊云科技 中构建,使用 Neptune 对数据进行群集可以轻松地从不连贯的数据中获得见解。结果是云原生应用程序的实时蓝图,该蓝图显示了每种风险及其关联资产。
要了解有关 Neptune 集群备份和恢复的更多信息,请参阅
作者简介
 吉尔·马克梅尔
是Devocean Security的首席技术官兼联合创始人。他拥有计算机科学学士学位,并且是以色列国防军精锐的8200情报部队的资深人士。
吉尔·马克梅尔
是Devocean Security的首席技术官兼联合创始人。他拥有计算机科学学士学位,并且是以色列国防军精锐的8200情报部队的资深人士。
 查尔斯·艾维
是 亚马逊云科技 亚马逊 Neptune 团队的高级图形架构师。十多年来,他一直使用知识图谱技术设计、实施和领导解决方案。
查尔斯·艾维
是 亚马逊云科技 亚马逊 Neptune 团队的高级图形架构师。十多年来,他一直使用知识图谱技术设计、实施和领导解决方案。
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。