我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
使用 Security Hub 中新的 “查找历史记录” 功能获取有关安全查找更改的详细信息
在当今不断变化的安全威胁格局中,安全团队越来越需要工具来检测和跟踪安全发现以保护其组织的资产。云安全态势管理的目标之一是及时有效地识别和处理安全发现。
随着调查结果数量的增加,跟踪每项调查结果的变化和采取的行动变得更加困难,对于及时有效地进行调查也变得更加重要。在这篇文章中,我们将向您展示如何使用Security Hub中新的查找历史记录功能来跟踪和理解安全发现的历史记录。
当查找提供者使用
batchImpor
tFindings API 更新某些字段(例如资源详细信息)时,就会对发现结果进行更新。作为用户,您可以在
寻找历史
Security Hub 中新的 “查找记录” 功能通过提供查找结果详细信息中不可变的更改历史记录来帮助您了解查找结果的状态。通过使用此功能,您可以跟踪每个发现的历史记录,包括更改字段之前和之后的值、更改的人员或内容以及更改的时间。这使您可以了解随着时间的推移对调查结果所做的更改以及调查结果的其余细节,从而简化了您对调查结果的操作方式,从而无需使用单独的工具或其他流程。此功能在可用 Security Hub 的 亚马逊云科技 区域免费提供,在新的或更新的发现中默认显示。也可以通过 Security Hub API 查看 “查找历史记录”。
要试用这项新功能,请打开 Sec
在以下示例中,调查结果已更新,然后使用调查结果的审阅者留下的解释性说明进行解决。使用 “查找历史记录”,您可以在查找结果的 “ 历史记录 ” 选项卡中查看以前的更新和事件。

图 1:“查找历史记录” 显示了该发现的最新更新
此外,您仍然可以在其 详细信息 选项卡中查看该发现的当前状态。
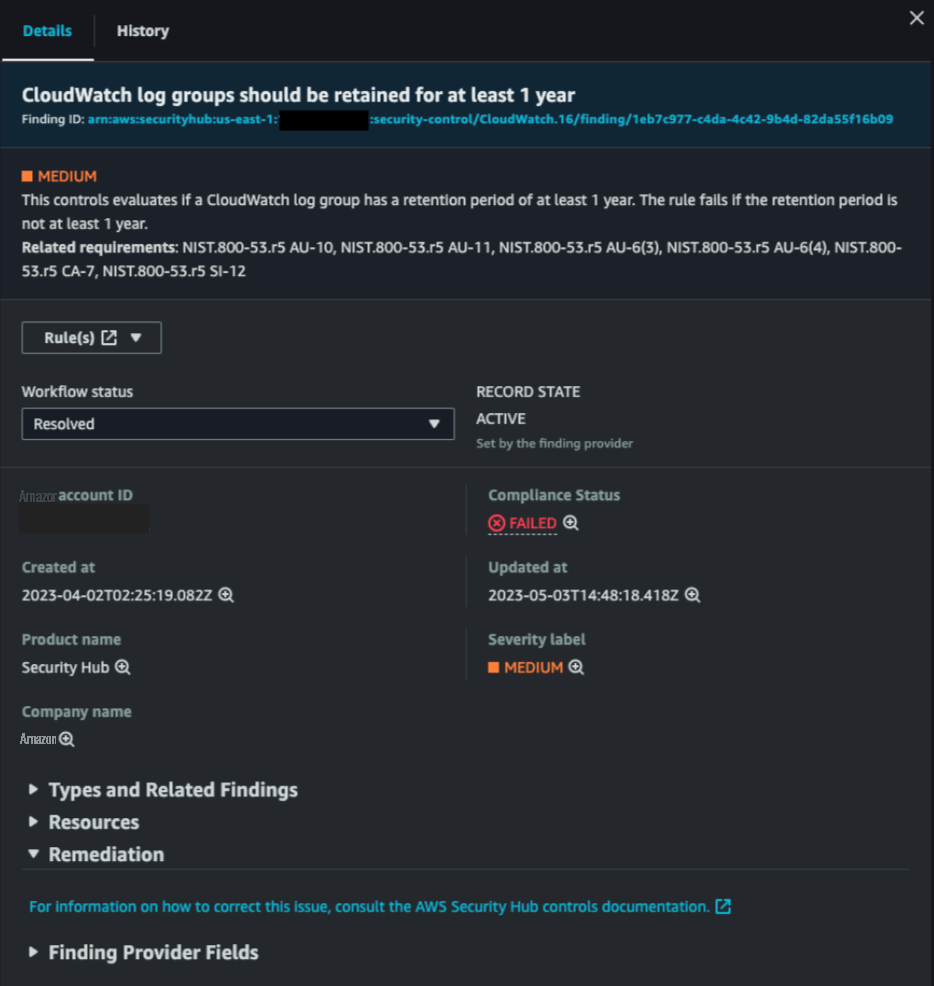
图 2:“查找详细信息” 显示安全检查或安全相关检测的记录
结论
借助 Security Hub 中全新的 “查找记录” 功能,您可以更好地了解活动和每项发现的更新,从而更有效地调查和应对潜在的安全风险。下次你开始在 Security Hub 中调查和回应安全调查结果时,首先要检查调查历史记录。
如果您对这篇文章有反馈,请在下面的评论部分提交评论。如果您对这篇文章有疑问,请在
想了解更多 亚马逊云科技 安全新闻?在
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。