我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
亚马逊云科技 Backup 的委托管理员支持
[更新:2022 年 12 月 13 日 — 在 步骤 2 下。亚马逊云科技 Organizations 控制台中的委托备份策略 、JSON 策略段落和 JSON 策略样本已更新。]
直到今天,备份管理员必须使用
借助 亚马逊云科技 Backup
在这篇博客文章中,我介绍了将 亚马逊云科技 Backup 策略管理和任务监控委托给成员账户的过程,并分享了配置这项新功能时的注意事项。
介绍添加委派管理员进行备份的流程
跨账户管理功能有两项功能。首先,能够在 亚马逊云科技 Organizations 中创建备份策略,其次是能够监控已应用备份策略的所有成员账户的跨账户备份、还原和复制任务。
先决条件
- 要委托 亚马逊云科技 Backup 策略管理,您需要您的 亚马逊云科技 组织管理账户的证书以及要委托管理的成员账号。
-
要委托 亚马逊云科技 Backup 任务监控,您需要在 亚马逊云科技 Backup 中启用跨账户管理。有关更多信息, 请参阅
文档 。
要将这两项功能委托给成员账户,需要执行两步流程。首先,在 亚马逊云科技 Backup 控制台中注册一个成员账户;然后,通过 亚马逊云科技 Organizations 控制台委派管理备份策略的权限。
步骤 1:在 亚马逊云科技 Backup 控制台中委派任务监控
1。使用您的管理账户证书登录并前往 亚马逊云科技 Backup 控制台。在 “设置” 下 ,向下滚动到新的 “ 委派管理员 ” 部分 。
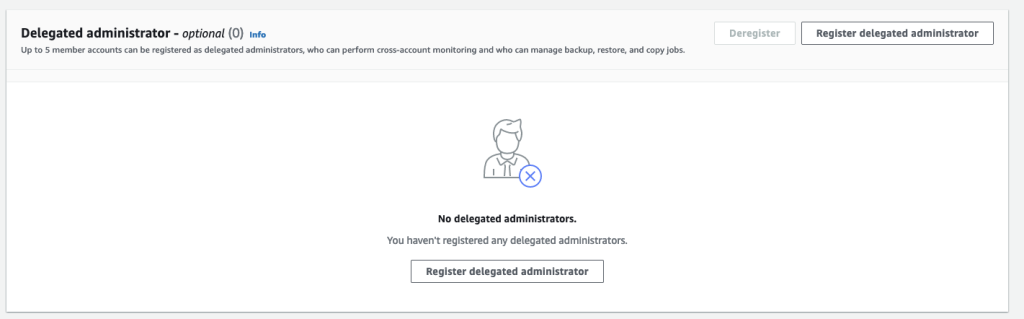
图 1:注册委派管理员
2。要注册委派管理员,请选择 注册委派管理员 。这将显示属于您的组织的账户列表。选择要委派访问权限的账户,然后选择 注册委派管理员 。
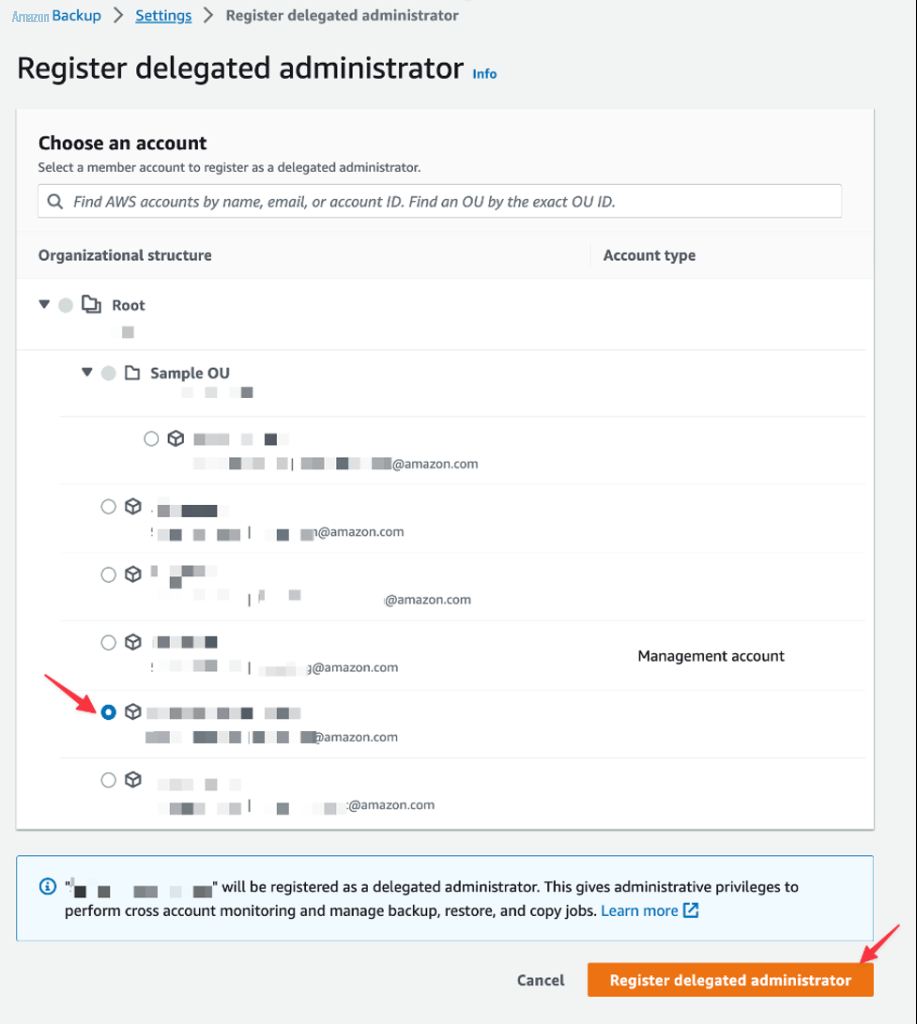
图 2:注册委派管理员
3。现在,在 “设置” 部分的 “委派管理员” 下方,您应该看到已注册的账户。
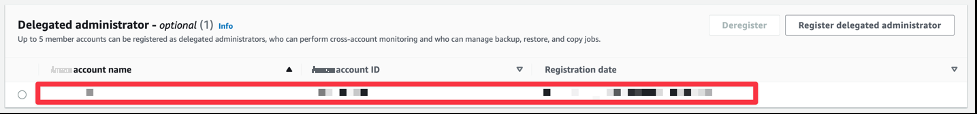
图 3:委派管理员注册摘要
注意:最多可以将 5 个成员帐户注册为委派管理员。
第 2 步。在 亚马逊云科技 Organizations 控制台中委派
1。在管理账户中,导航至设置,向下滚动,您将看到一个名为 亚马逊云科技 Organizati ons 委托管理员 的新部分 。选择 委托 ,如图 4 所示。
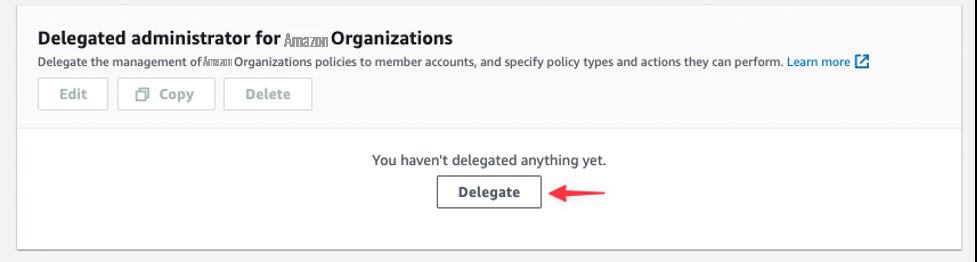
图 4:亚马逊云科技 Organizations 的委派管理员
2。在 JSON 编辑器中,使用与上一步中在 亚马逊云科技 Backup 中监控委托任务相同的成员账户 ID 定义委托 亚马逊云科技 Backup 管理的策略。
作为参考,请使用以下 JSON 策略示例,该策略提供全面管理备份策略的权限。请记住将 亚马逊云科技 成员账户 ID 替换为您委托访问权限的账户 ID ,将 亚马逊云科技 管理账户 ID 替换为您的 亚马逊云科技 Organizations 管理账户的账户 ID 。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowOrganizationsRead",
"Effect": "Allow",
"Principal": {
"AWS": "AWS-member-account-ID"
},
"Action": [
"organizations:Describe*",
"organizations:List*"
],
"Resource": "*"
},
{
"Sid": "AllowBackupPoliciesCreation",
"Effect": "Allow",
"Principal": {
"AWS": "AWS-member-account-ID"
},
"Action": [
"organizations:CreatePolicy"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"organizations:PolicyType": "BACKUP_POLICY"
}
}
},
{
"Sid": "AllowBackupPoliciesModification",
"Effect": "Allow",
"Principal": {
"AWS": "AWS-member-account-ID"
},
"Action": [
"organizations:DescribePolicy",
"organizations:UpdatePolicy",
"organizations:DeletePolicy"
],
"Resource": [
"arn:aws:organizations::AWS-management-account-ID:policy/*/backup_policy/*" ],
"Condition": {
"StringEquals": {
"organizations:PolicyType": "BACKUP_POLICY"
}
}
},
{
"Sid": "AllowBackupPoliciesAttachmentAndDetachmentToAllAccountsAndOUs",
"Effect": "Allow",
"Principal": {
"AWS": "AWS-member-account-ID"
},
"Action": [
"organizations:AttachPolicy",
"organizations:DetachPolicy"
],
"Resource": [
"arn:aws:organizations::AWS-management-account-ID:root/*",
"arn:aws:organizations::AWS-management-account-ID:ou/*",
"arn:aws:organizations::AWS-management-account-ID:account/*",
"arn:aws:organizations::AWS-management-account-ID:policy/*/backup_policy/*"
],
"Condition": {
"StringEquals": {
"organizations:PolicyType": "BACKUP_POLICY"
}
}
}
]
}
如果您需要向多个成员账户委派权限,请使用主体部分中的数组来添加多个账户 ID。以下示例说明了该部分在使用多个账户 ID 时的外观。
"Principal" : {
"AWS": [
"123456789012",
"555555555555"
]
}
验证
完成上述步骤后,您可以验证是否已委派所需的权限。在 亚马逊云科技 Backup 控制台中登录注册为委托管理员的账户,然后前往 “设置”。在 “委派管理员” 部分下,您应该看到注册的成员帐户。
在 亚马逊云科技 Backup 控制台中,从屏幕左侧的侧面菜单中选择跨账户监控,然后确认您可以监控 亚马逊云科技 组织内多个账户的备份、还原和复制活动的状态。最后,转到屏幕左侧的备份策略,验证您可以创建、删除和修改备份策略。
正在清理
委托管理员权限不会产生任何额外费用,但如果您想恢复通过本博客文章实施的配置,则可以在 亚马逊云科技 Backup 控制台中注销委派成员账户,并在 亚马逊云科技 Organizations 委派管理员部分删除该策略。
结论
在这篇文章中,我们展示了如何为 亚马逊云科技 Backup 配置委托管理、在无需访问 亚马逊云科技 Organizations 管理账户的情况下将 亚马逊云科技 Backup 的管理和跨账户管理功能委托给非管理型 亚马逊云科技 账户。这遵循了 亚马逊云科技 推荐的最佳实践,即限制对管理账户的访问,因为您不再需要使用管理账户来执行日常数据保护任务。
要了解有关 亚马逊云科技 Backup 跨账户管理和委托管理的更多信息,请参阅
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。