我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
使用 亚马逊云科技 资源访问管理器配置对共享资源的精细访问权限
您可以使用
使用 亚马逊云科技 RAM 共享资源时,您可以指定账户可以执行的操作以及共享资源的访问条件。亚马逊云科技 RAM 提供
这篇博客文章将引导您了解如何使用客户管理权限来定制资源访问权限以满足您的业务和安全需求。客户托管权限可帮助您对使用 亚马逊云科技 RAM 共享 的资源遵循
注意事项
开始之前,请查看《
解决方案概述
许多 亚马逊云科技 客户通过
您将使用拥有 IPAM 池的网络账户与开发 OU 中的账户共享池。为此,您可以通过 亚马逊云科技 RAM 创建资源共享和客户管理权限。在此示例中(如图 1 所示),网络账户和开发 OU 位于同一个组织中。开发 OU 中的账户仅需要分配无类域间路由 (CIDR) 范围所需的权限,无需查看 IPAM 池的详细信息。您将进一步优化对共享 IPAM 池的访问权限,以便只有
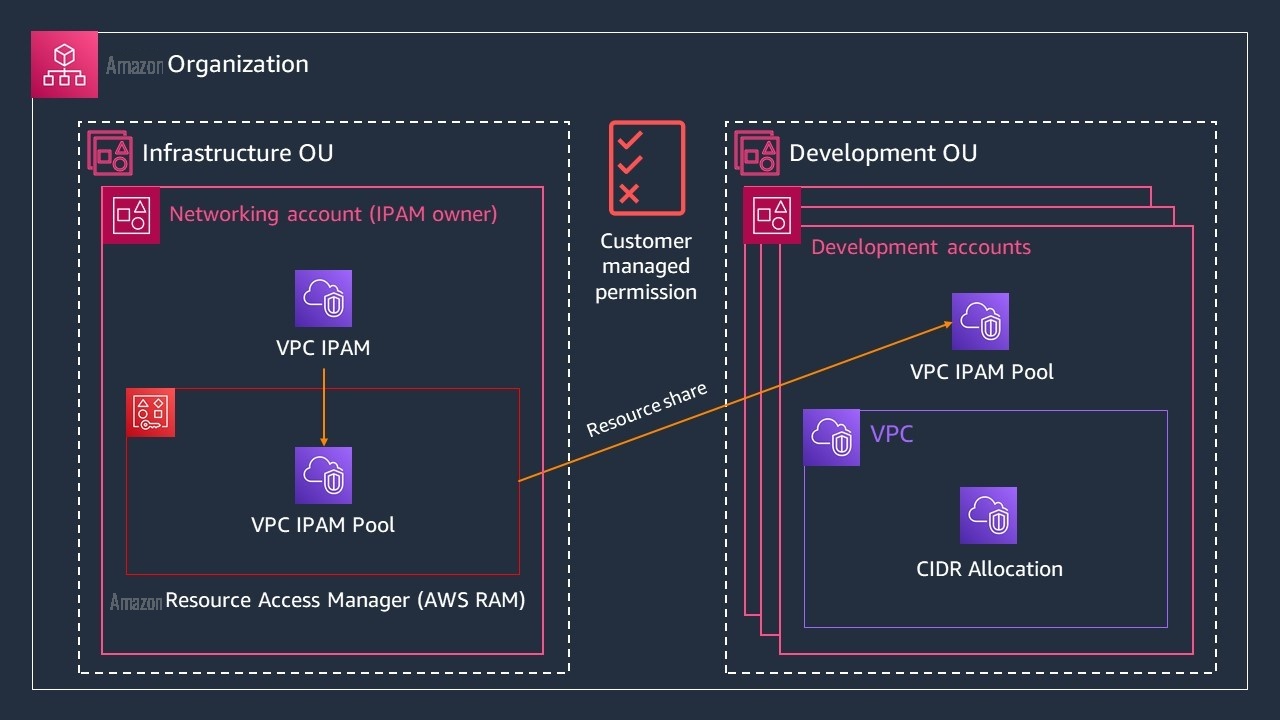
图 1:将您的 IPAM 池从基础架构组织单元中的网络账户共享到开发 OU 中的账户的多账户图
先决条件
在本演练中,您必须具备以下先决条件:
-
已经预配置了 IPAM 池 的亚马逊云科技 账户 (网络账户)。 在此示例中,在名为 ipam-vpc-pool-use1-dev 的网络账户中创建一个 IPAM 池。 由于您使用 亚马逊云科技 RAM 在同一 亚马逊云科技 区域的账户之间共享资源,因此请在开发账户访问池的同一区域预置 IPAM 池。 - 带有关联开发账户的 亚马逊云科技 OU,可与之共享 IPAM 池。在此示例中,这些账户位于您的开发 OU 中。
-
有权在网络账户和开发账户中执行
IPAM 和亚马逊云科技 RAM 操作的 IAM 角色或用户。
使用最低权限与开发 OU 共享您的 IPAM 池
在本节中,您将网络账户中的 IPAM 池共享到开发 OU 中的账户,并授予最低权限权限。为此,您需要创建一个资源共享,其中包含您的 IPAM 池、您的 IPAM 池客户管理权限以及要与之共享 IPAM 池的 OU 负责人。资源共享包含您要共享的资源、要与之共享资源的委托人以及向接收资源的账户授予资源访问权限的托管权限。您可以将 IPAM 池添加到现有资源共享,也可以创建新的资源共享。根据您的工作流程,您可以在 Amazon VPC IPAM 或 亚马逊云科技 RAM 控制台中开始创建资源共享。
从 Amazon VPC IPAM 控制台启动新的资源共享
-
以您的网络账户登录
亚马逊云科技 管理控制台 。对于 功能 ,选择亚马逊 VPC IP 地址管理器 控制台。 - 选择 ipam-vpc-pool-use1-dev ,它是作为先决条件的一部分进行配置的。
- 在 IPAM 池详细信息页面上,选择 资源共享 选项卡。
-
选择 “
创建资源共享
” 。
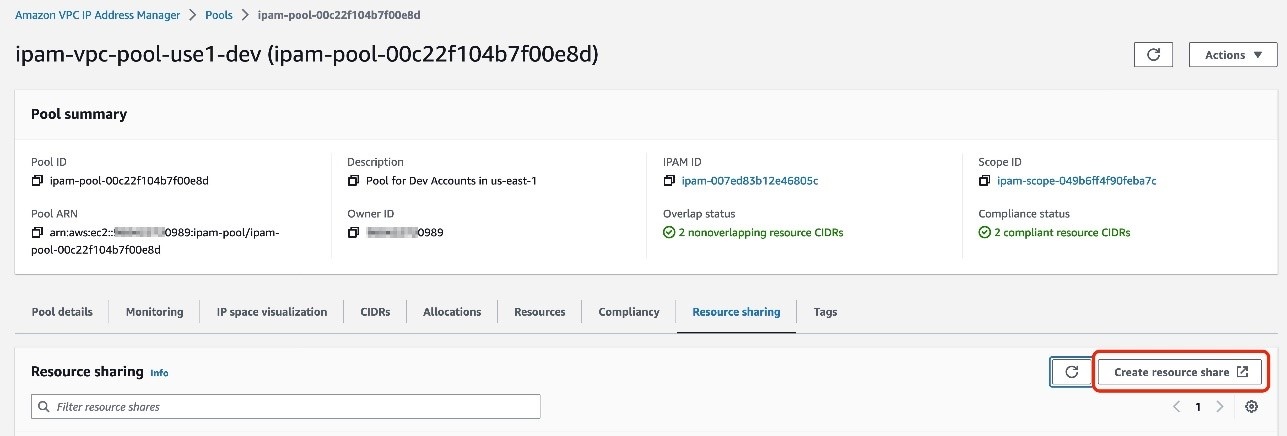
图 2:创建资源共享以共享您的 IPAM 池
或者,您可以从 亚马逊云科技 RAM 控制台启动新的资源共享。
从 亚马逊云科技 RAM 控制台启动新的资源共享
-
以您的网络账户登录
亚马逊云科技 管理控制台 。对于 服务 ,选择资源访问管理器 控制台。 - 选择 “ 创建资源共享 ” 。
接下来,指定资源共享详细信息,包括名称、资源类型和要共享的特定资源。请注意,资源共享创建过程的步骤位于 亚马逊云科技 RAM 控制台的左侧。
指定资源共享详情
- 对于 名称 ,输入 ipam-s hared-dev-pool 。
- 对于 “选择资源类型 ” ,选择 IPAM 池 。
- 对于 资源 ,请从您拥有的 IPAM 池 ARN 列表中选择要共享的 IPAM 池的亚马逊资源名称 (ARN)。
-
选择 “
下一步
” 。
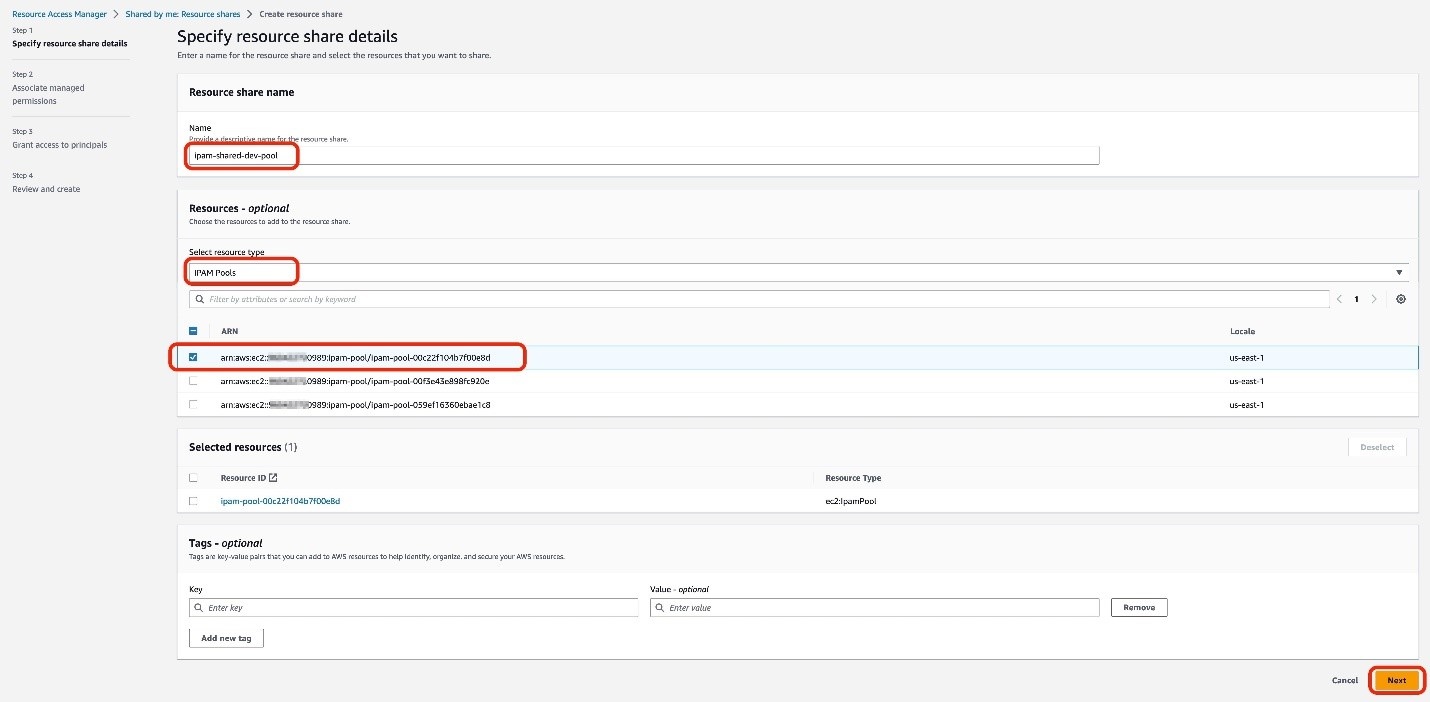
图 3:指定要在资源共享中共享的资源
配置客户管理权限
在此示例中,开发 OU 中的账户需要分配 CIDR 范围所需的权限,但不需要查看 IPAM 池详细信息的权限。现有的 亚马逊云科技 托管权限同时授予读取和写入权限。因此,您需要创建客户管理权限,以细化开发 OU 中账户的资源访问权限。使用客户管理权限,您可以选择和定制开发账户可以在 IPAM 池上执行的操作,例如只写操作。
在本节中,您将创建客户托管权限、配置托管权限名称、选择资源类型并选择允许使用共享资源执行的操作。
创建和创作客户管理权限
- 在 关联托管权限 页面上,选择 创建客户管理权限。 这将打开一个带有 “ 创建客户管理权限 ” 页面的新浏览器选项卡。
- 在 创建客户管理权限 页面上,输入 my-ipam-cmp 作为 客户 管理的权限名称。
- 确认 资源类型 为 ec2: I pamPool。
- 在 策略模板 部分 的可视化编辑器 选项卡上,仅 选中 “ 写入 ” 复选框。这将自动检查所有可用的写入操作。
-
选择 “
创建客户管理权限”
。
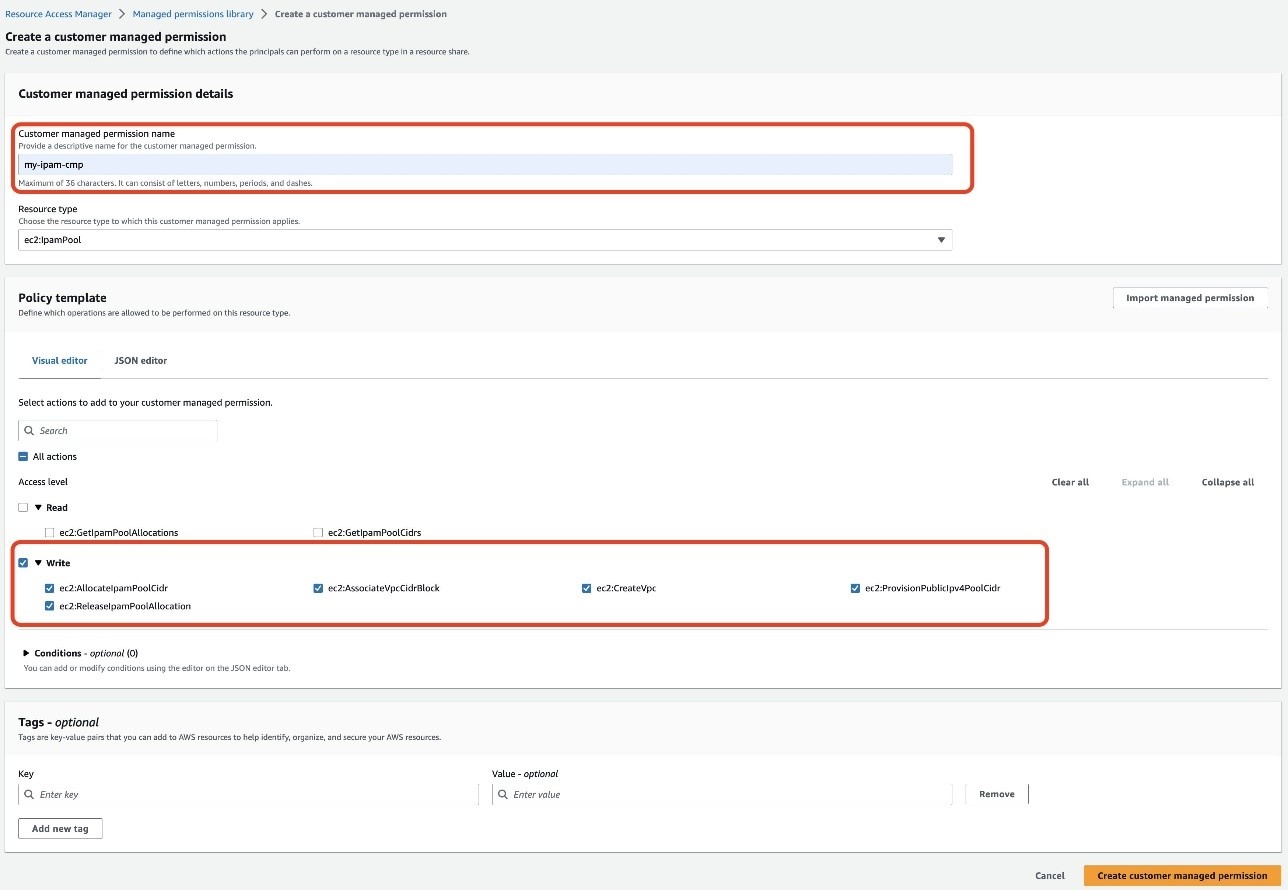
图 4:仅使用写入操作创建客户管理权限
现在您已经创建了客户管理权限,您必须将其关联到您的资源共享。
关联您的客户管理权限
- 返回之前的 助理管理权限 页面。这很可能位于单独的浏览器选项卡中。
-
选择刷新图标
 。
。
- 从下拉 菜单中选择 my-ipam-cmp 。
- 查看策略模板,然后选择 Next 。
接下来,选择要与之共享 IPAM 池的 IAM 角色、IAM 用户、亚马逊云科技 账户、亚马逊云科技 OU 或组织。在此示例中,您与账户中的 OU 共享 IPAM 池。
向校长授予访问权限
- 在 向校长 授予访问权限 页面上,选择 仅 允许与您的组织 共享 。
- 对于 选择主要人类型 ,选择 组织单位 (OU) 。
- 输入开发 OU 的 ID。
- 选择 “ 添加 ” ,然后选择 “ 下一步 ” 。
-
选择 “
创建资源共享
” 以完成资源共享的创建。
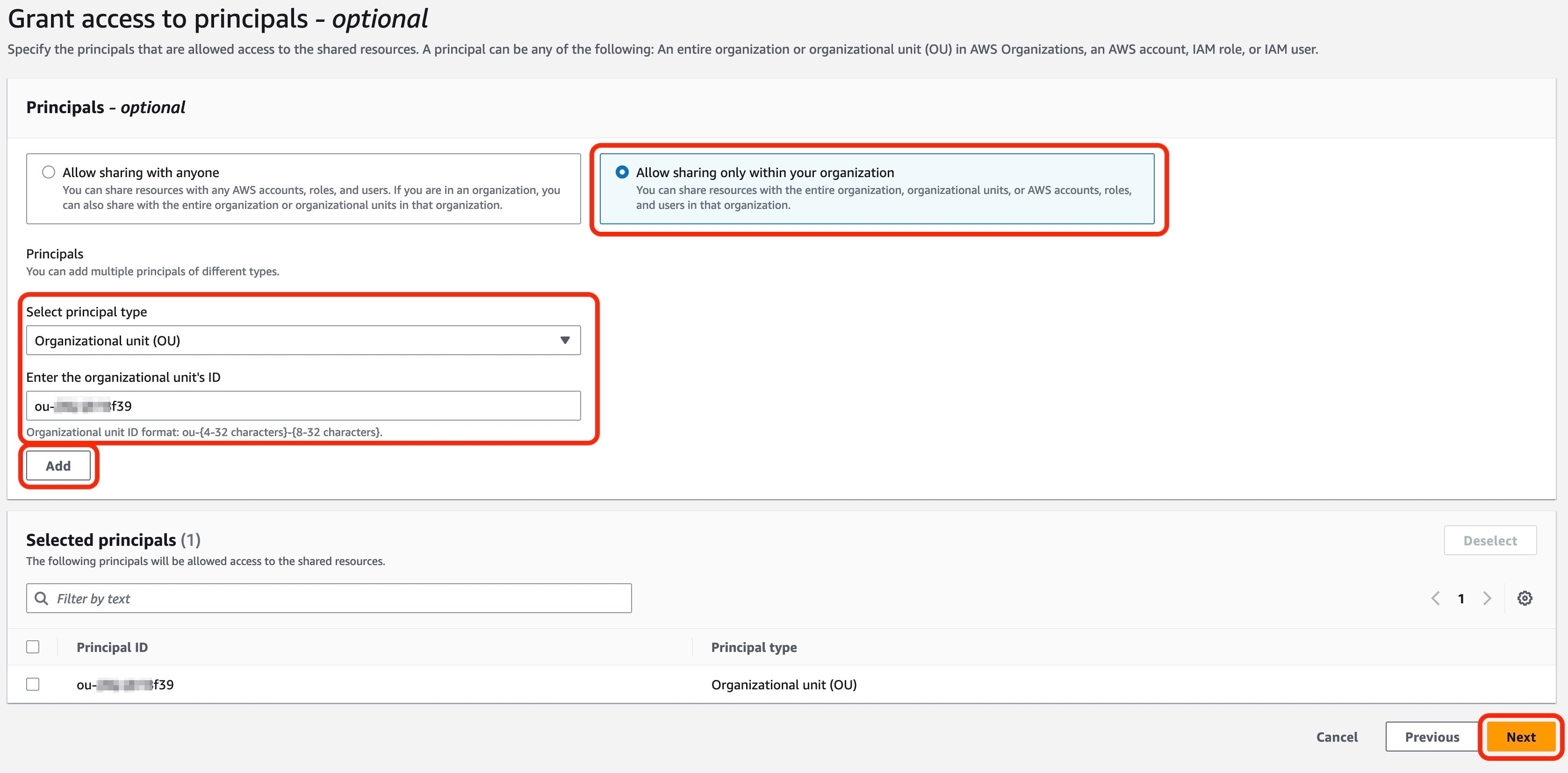
图 5:向资源共享中的委托人授予访问权限
验证客户管理权限
现在,让我们验证客户管理的权限是否按预期运行。在本节中,您将验证开发账户无法查看 IPAM 池的详细信息,以及是否可以使用同一个账户创建 IPAM 池的 VPC。
验证您的开发 OU 中的账户无法查看 IPAM 池的详细信息
-
在开发 OU 中以账户 身份登录
亚马逊云科技 管理控制台 。对于 功能 ,选择亚马逊 VPC IP 地址管理器 控制台。 - 在左侧导航窗格中,选择 池 。
- 选择 ipam-shared-dev-pool 。您将无法查看 IPAM 池的详细信息。
验证您的开发 OU 中的账户是否可以使用 IPAM 池创建新的 VPC
-
在开发 OU 中以账户 身份登录
亚马逊云科技 管理控制台 。对于 服务 ,选择VPC 控制台。 - 在 VPC 控制面板 上 ,选择 创建 VPC 。
- 在 创建 VPC 页面上,选择 仅限 VPC 。
- 对于 名称 ,请输入 my-dev-vpc 。
- 选择 IPam 分配的 IPv4 网段 。
- 选择与您的开发账户共享的 IPAM 池的 ARN。
- 对于 网络掩码 ,选择 /24 256 IP 。
-
选择
创建 VPC
。您已成功创建一个 VPC,其IPAM 池与您的开发 OU 中的账户共享。
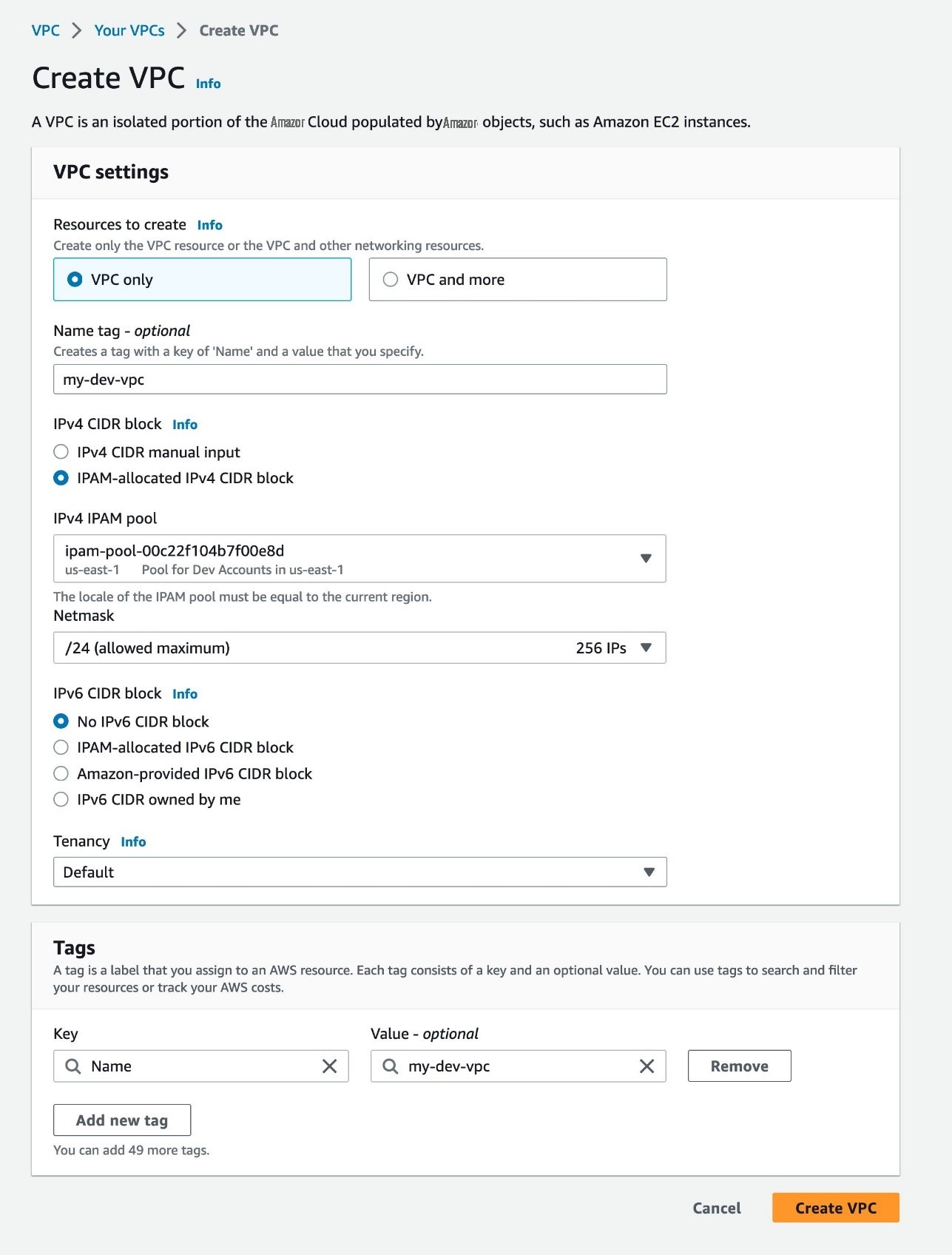
图 6:创建 VPC
更新客户管理权限
您可以创建客户托管权限的新版本,以重新调整和更新使用 亚马逊云科技 RAM 共享的资源的访问粒度。例如,您可以在客户管理权限中添加一个条件,以便只有标有特定委托人标签的 IAM 用户或角色才能访问和执行对使用 亚马逊云科技 RAM 共享的资源的允许操作。如果您需要更新客户管理权限(例如,在测试之后或随着业务和安全需求的发展),则可以创建和保存相同客户管理权限的新版本,而不是创建全新的客户管理权限。例如,您可能需要将开发账户的访问配置调整为只读操作,并将测试账户的访问权限配置重新调整为读写操作。新版本的权限不会自动应用于您的现有资源共享,您必须将其明确应用于这些共享才能生效。
创建客户管理权限的版本
-
以您的网络账户登录
亚马逊云科技 管理控制台 。对于 服务 ,选择资源访问管理器 控制台。 - 在左侧导航窗格中,选择 托管权限库 。
- 在 “ 按文本 筛选 ” 中 ,输入 my-ipam-cmp,然后选择 my-ipam-cmp 。 您也可以选择 “ 任何类型 ” 下拉菜单,然后选择 “ 客户管理 ”,将托管权限列表范围缩小 到仅限您的客户管理权限。
- 在 my-ipam-cmp 页面上,选择创建版本。
- 您可以通过添加条件来使客户管理的权限更加精细。 在 “ 为 my-ipam-cmp 创建客户管理权限 ” 页面上的 “ 策略模板 ” 部分下,选择 JSON 编辑器。
-
使用
aws: PrincipalTag
添加一个条件 ,仅允许标有 tea
m = 网络
的用户或角色 访问共享 IPAM 池。
“条件”:{“StringEquals”:{“aws: PrincipalTag/Team”:“网络”}} -
选择
创建版本
。此新版本将自动设置为您的客户管理权限的默认版本。因此,使用客户管理权限的新资源共享将使用新版本。
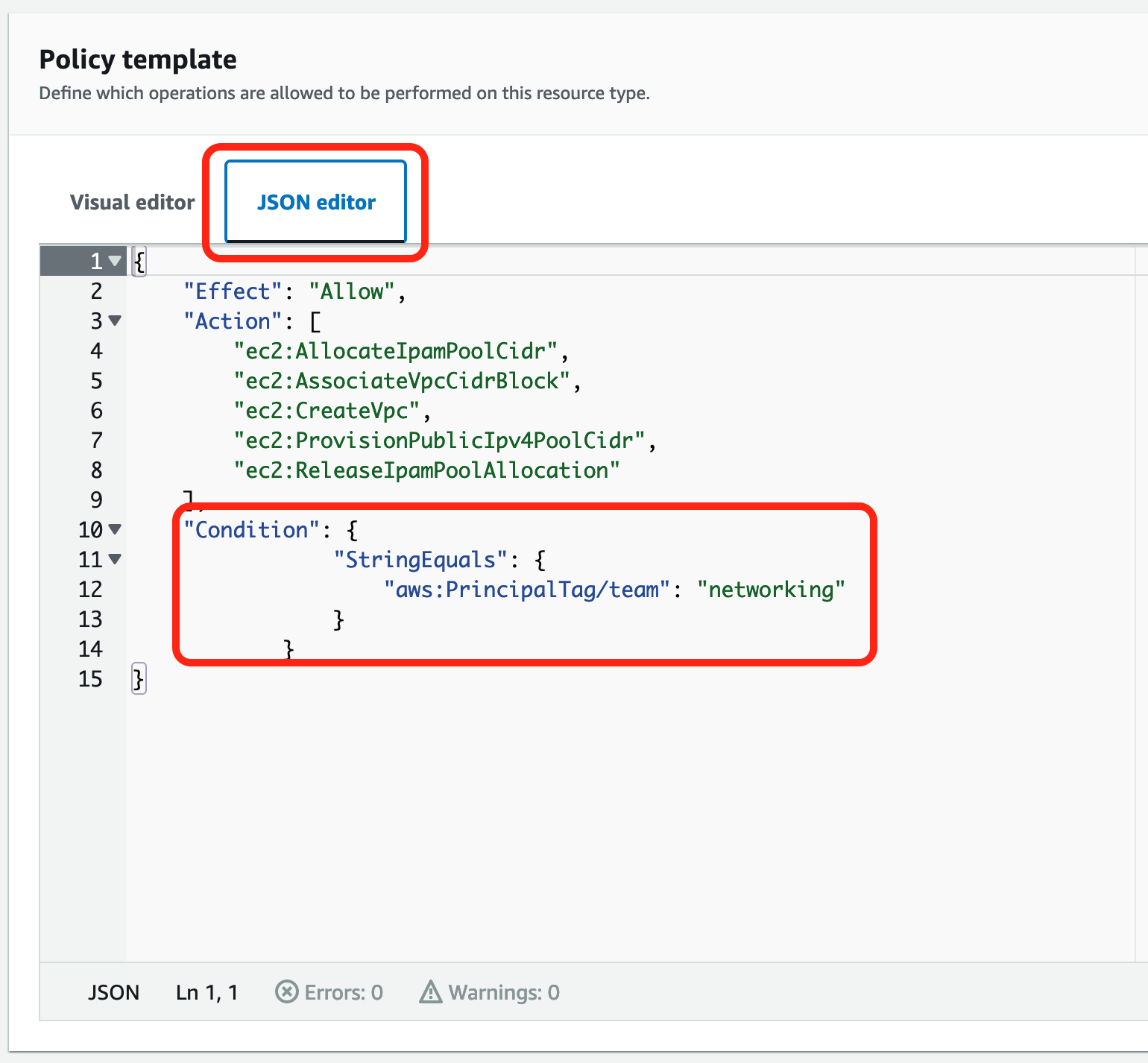
图 7:使用 亚马逊云科技 : principalTag 更新您的客户管理权限并添加条件声明
注意: 既然您已经有了新版本的客户管理权限,则必须将其明确应用于现有资源共享才能生效。
将新版本的客户管理权限应用于现有资源共享
- 在 my-ipam-cmp 页面的 托管权限版本下 ,选择版本 1 。
- 选择 “ 关联的资源共享 ” 选项卡。
- 找到 ipam-shared-dev-pool ,然后在当前版本号旁边,选择更新到默认版本。 这将使用您的 my-ipam-cmp 客户管理权限的新版本更新您的 ipam-shared-dev-pool 资源共享。
要验证您更新的客户管理权限,请参阅本文前 面的 “ 验证客户管理权限 ” 部分。确保使用标有 tea m = networking 的 IAM 角色或用户登录, 然后重复该部分的步骤以验证更新后的客户管理权限。如果您使用未标有 tea m = n etworking 的 IAM 角色或用户 ,您将无法从 IPAM 池中分配 CIDR,也无法创建 VPC。
清理
要删除前面示例创建的资源,请执行以下操作:
- 从 亚马逊云科技 RAM 控制台中删除资源共享。
- 从 IPAM 池中取消配置 CIDR。
- 删除您创建的 IPAM 池。
摘要
这篇博文介绍了在 亚马逊云科技 RAM 中使用客户托管权限的示例。在跨账户共享资源时,亚马逊云科技 RAM 带来了简单性、一致性和信心。在示例中,您使用 亚马逊云科技 RAM 向开发 OU 中的账户共享 IPAM 池,配置了精细的资源访问控制,并遵循了最低权限的最佳实践,仅向开发 OU 中的账户授予使用共享 IPAM 池执行特定任务所需的权限。在示例中,您还创建了客户管理权限的新版本,以重新调整使用 亚马逊云科技 RAM 共享的资源的访问粒度。
要了解有关 亚马逊云科技 RAM 和客户管理权限的更多信息,请参阅
如果您对这篇文章有反馈,请在下面的
评论
部分提交评论。如果您对这篇文章有疑问,
想了解更多 亚马逊云科技 安全新闻?在
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。