我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
亚马逊云科技 SAM 对 HashiCorp Terraform 的支持现已正式上线
2022 年 11 月,亚马逊云科技
Terraform 和 亚马逊云科技 SAM 都是开源框架,允许开发人员将基础设施定义为代码 (IaC)。开发人员可以像共享代码一样对基础架构定义进行版本控制和共享。但是,由于 亚马逊云科技 SAM 是专门为无服务器设计的,因此它包括专为无服务器开发而设计的命令行接口 (CLI)。CLI 使开发人员能够使用本地仿真器以及构建和部署工具创建、调试和部署无服务器应用程序。在此版本中,亚马逊云科技 SAM 还将这些工具的子集制作给 Terraform 用户。
地形支持
模块可以为 Lambda 函数和层构建部署工件。此外,该模块会自动生成 亚马逊云科技 SAM 与 Terraform 资源连接所需的元数据。要使用原生 Terraform 资源,请参阅
正在下载代码
要了解 亚马逊云科技 SAM 对 Terraform 的支持,请访问 a
git 克隆 https://github.com/aws-samples/aws-sam-terraform-examples
cd ga
在这个目录中,有两个演示应用程序。
cd api_gateway_v1/tf-resources除非另有说明,否则本文中的示例引用了 api_gateway_ v1 应用程序。
代码结构
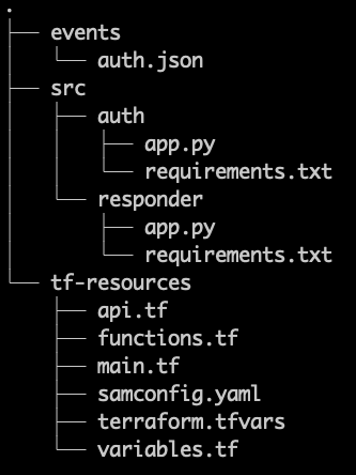
代码结构图
Terraform 支持将 iaC 分散到多个文件中。因此,开发人员通常将所有 Terraform 文件收集在一个目录中,并将资源文件保存在其他地方。示例应用程序是这样配置的。
任何 Terraform 或 亚马逊云科技 SAM 命令都必须从 主.tf 文件(在本例中为 tf-resources 目录)的位置运行。 由于 亚马逊云科技 SAM 命令通常从项目根目录运行,因此 亚马逊云科技 SAM 有一个支持嵌套结构的命令。如果从嵌套文件夹运行 相同的编译 命令,请将 terraform-project-root-project-root-path 标志 以及指向项目根目录的相对路径 或绝对路径传递。
本地调用
Terraform 的预览版支持本地调用,但该团队通过支持 Serverless.TF 简化了体验。演示应用程序中有两个功能。响应器函数是 API 网关端点的后端集成,而身份验证函数是自定义授权器。在 f
响应器功能
module "lambda_function_responder" {
source = "terraform-aws-modules/lambda/aws"
version = "~> 6.0"
timeout = 300
source_path = "${path.module}/src/responder/"
function_name = "responder"
handler = "app.open_handler"
runtime = "python3.9"
create_sam_metadata = true
publish = true
allowed_triggers = {
APIGatewayAny = {
service = "apigateway"
source_arn = "${aws_api_gateway_rest_api.api.execution_arn}/*/*"
}
}
}
有两个重要参数:
- source_path ,它指向本地文件夹。由于这不是压缩文件,因此 Serverless.tf 会根据需要构建工件。
- create_sam_dat a,它生成 亚马逊云科技 SAM 查找必要文件和模块所需的元数据。
要在本地调用该函数,请运行以下命令:
-
运行 build 运行任何构建脚本 sam build
root-p--hook-name terrafor m--terraform-project-root-project- -
运行本地调用以调用所需的 Lambda 函数 sam 本地调用--h
tion.this [0] 'ook-name terrafor m--terraform-project-root-project-project-project-project-project-project_responder.aws_lambda_func
由于该项目是 Terraform,因此需要使用值为 terrafor m 的 挂钩名称 参数才能让 亚马逊云科技 SAM 知道如何进行。函数名称是模块名称及其变为的资源类型的组合。如果您不确定名称,请运行不带名称的命令:
sam local invoke --hook-name terraform亚马逊云科技 SAM 会对模板进行评估。如果只有一个函数,亚马逊云科技 SAM 会继续调用它。如果有多个(例如此处的情况),亚马逊云科技 SAM 会询问您是哪一个,并提供选项列表。
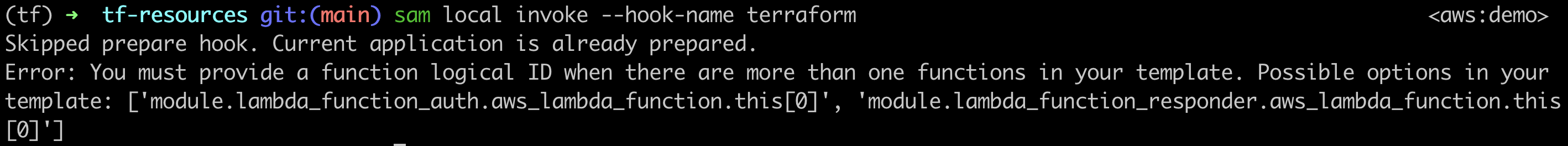
错误文本示例
身份验证函数
授权器函数需要一些输入数据作为模拟事件。要为 api_gateway_v1 项目生成模拟事件,请执行以下操作:
sam local generate-event apigateway authorizer对于 api_gateway_v2 项目,请使用:
sam local generate-event apigateway request-authorizer
由此产生的事件是不同的,因为 API Gateway REST 和 HTTP API 可以以不同的方式处理自定义授权器。在这些示例中,REST 使用标准
每个示例都已经在 events /auth.json 中包含了格式正确的测试事件 。要调用 Auth 函数,请运行以下命令:
sam local invoke --hook-name terraform 'module.lambda_function_auth.aws_lambda_function.this[0]' -e events/auth.json由于应用程序没有更改,因此无需再次运行 sam build 命令。
本地启动 api
现在,您可以使用正式发布的版本来模拟 API Gateway 的本地版本。每个示例都有两个端点。一个端点处于打开状态,自定义授权器保护另一个端点。两者都返回相同的响应:
{
“message”: “Hello TF World”,
“location”: “ip address”
}要启动本地模拟器,请运行以下命令:
sam local start-api –hook-name terraform亚马逊云科技 SAM 启动模拟器并公开两个终端节点以进行本地测试。
打开端点
使用
curl --location http://localhost:3000/open本地仿真器处理请求并在终端窗口中提供响应。模拟器还包括来自 Lambda 函数的日志。
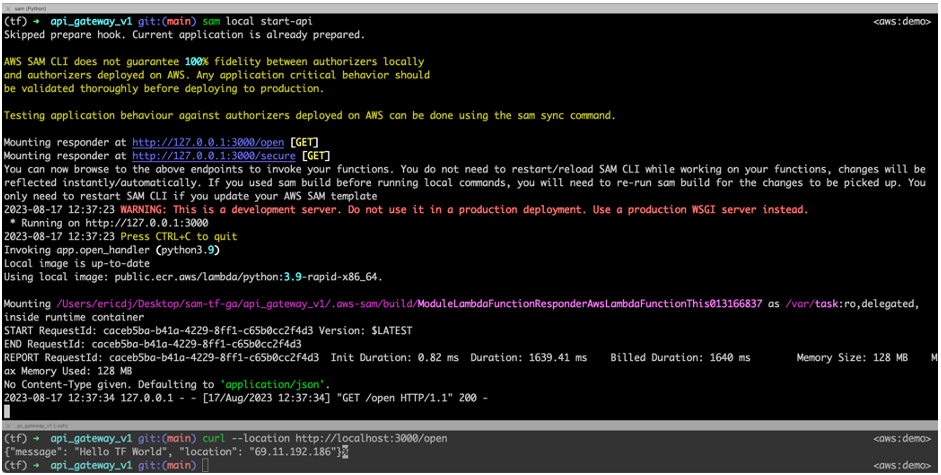
打开端点示例输出
身份验证端点
测试安全端点并传递额外的必需标 头 my header:
curl -v --location http://localhost:3000/secure --header 'myheader: 123456789'端点返回带有 “Hello TF World” 消息的授权响应。使用无效的标头值再次尝试端点:
curl --location http://localhost:3000/secure --header 'myheader: IamInvalid'端点返回未经身份验证的响应。
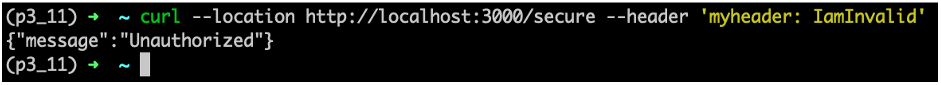
未经身份验证的响应
参数
将 亚马逊云科技 SAM 与 Terraform 一起使用时,有几种选择:
- 挂钩名称 :在使用 Terraform 时,每个命令都必须使用挂钩名称。这会告知 亚马逊云科技 SAM 该项目是一个 Terraform 应用程序。
- skip-prepare-infra: 亚马逊云科技 SAM 使用 terraform plan 命令识别和处理所有必需的工件。但是,它只能在添加或修改新资源时运行。此选项可防止 亚马逊云科技 SAM 运行 terraform 计划命令。如果此标志已通过但计划不存在,则 亚马逊云科技 SAM 会忽略该标志并运行 terraform plan 命令。
- Prepare-infra: 强制 亚马逊云科技 SAM 运行 terraf orm plan 命令。
- Terraform-project-root-Path:将当前目录 替换为项目的根目录。 你可以使用绝对路径( /path/to/project/root )或相对路径( ../或.../... / )。
- Terraform-Plan-File: 允许开发人员指定特定的 Terraform 计划文件 。此命令还允许 Terraform 用户使用本地命令。
组合这些选项可以创建较长的命令:
sam build --hook-name terraform --terraform-project-root-path ../要么
sam local invoke –hook-name terraform –skip-prepare-infra 'module.lambda_function_responder.aws_lambda_function.this[0]'
您可以使用
version: 0.1
default:
global:
parameters:
hook_name: terraform
skip_prepare_infra: true
build:
parameters:
terraform_project_root_path: ../通过设置这些默认值,该命令现在缩短了:
sam local invoke 'module.lambda_function_responder.aws_lambda_function.this[0]'亚马逊云科技 SAM 现在知道这是一个 Terraform 项目,除非缺少 Terraform 计划,否则会跳过准备任务。如果需要更新计划,请添加 —prepare-infra 标志以覆盖默认设置。
部署和远程调试
这些项目中的应用程序是常规的 Terraform 应用程序。将它们像任何其他 Terraform 项目一样部署。
terraform plan
terraform apply目前,亚马逊云科技 SAM 加速器不支持 Terraform 项目。但是,由于 Terraform 使用 API 方法进行部署,因此无服务器应用程序可以快速部署。使用第三方手表和 terraform apply —auto-approve 命令来近似这种体验。
要进行日志记录,请使用 sam logs 命令。有关跟踪一项或所有资源日志的示例,请参阅项目的部署输出。
HashiCorp 云平台
结论
HashiCorp Terraform 是一个流行的 iaC 框架,用于在 亚马逊云科技 云中构建应用程序。亚马逊云科技 SAM 是一个 IaC 框架,CLI 专为帮助开发人员构建无服务器应用程序而设计。
这篇博客介绍了对 Terraform 的新 亚马逊云科技 SAM 支持,以及开发人员如何将它们结合起来以最大限度地提高开发体验。该博客介绍了在本地调用单个函数、在本地模拟 API Gateway 端点以及在部署之前在本地测试 Lambda 授权器。最后,该博客部署了应用程序并使用 亚马逊云科技 SAM 来监控已部署的资源。
如需更多无服务器学习资源,请访问
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。