我们使用机器学习技术将英文博客翻译为简体中文。您可以点击导航栏中的“中文(简体)”切换到英文版本。
亚马逊云科技 AppSync 私有 API 的架构模式
使用私有 API,您的私有网络中的消费者无需通往互联网的路由即可与 API 端点通信。在这篇博客中,我们将介绍五种常见的架构模式,以建立与您的 亚马逊云科技 AppSync 私有 API 的连接。这些架构模式包括:
- 通过 VPC 连接到 AppSync 私有 API
- 通过 VPC 连接到 AppSync 私有 API
- 跨账户连接到 AppSync 私有 API
- 与 AppSync 私有 API 的混合连接
- 使用 API 网关代理 AppSync 私有 API
AppSync 私有 API 可通过接口 VPC 端点 DNS 名称或 AppSync API GraphQL 终端节点(如果在创建 VPC 端点时启用了 “私有 DNS 名称”)进行访问,如下所示。
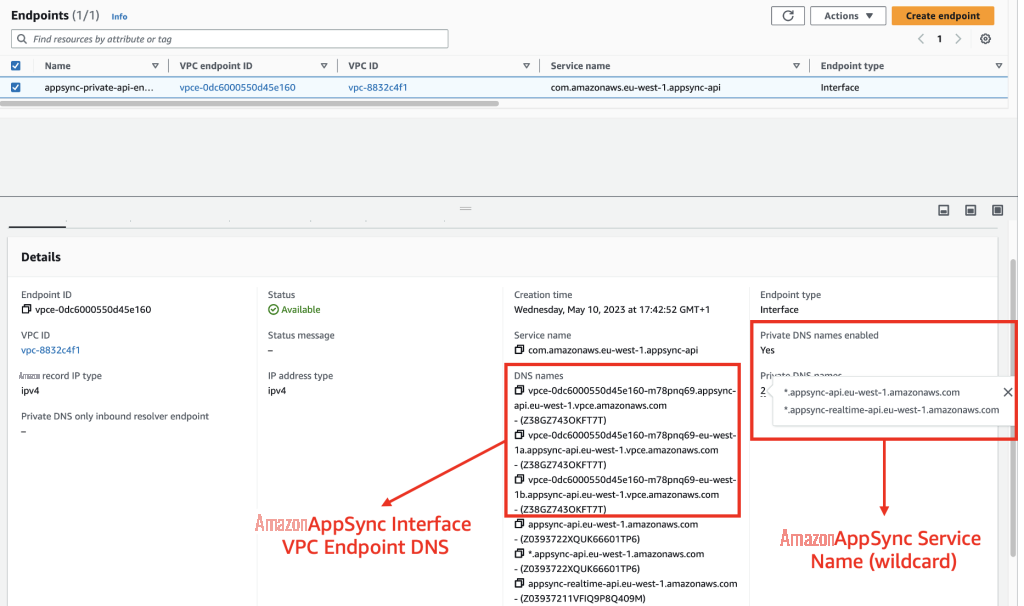
图 1:亚马逊云科技 AppSync 接口 VPC 终端节点配置
在以下部分中,我们将介绍每种架构模式,并解释如何设置架构以满足您的用例。我们将解释 API 使用者使用 AppSync API GraphQL 端点或接口 VPC 端点公有 DNS 主机名调用 API 端点所需的配置。
模式 1:与 AppSync 私有 API 的单个 VPC 连接
在这种模式 中,有两个 API 使用者(EC2 实例)托管在与 AppSync 接口终端节点相同的 VPC 中,如下所示。
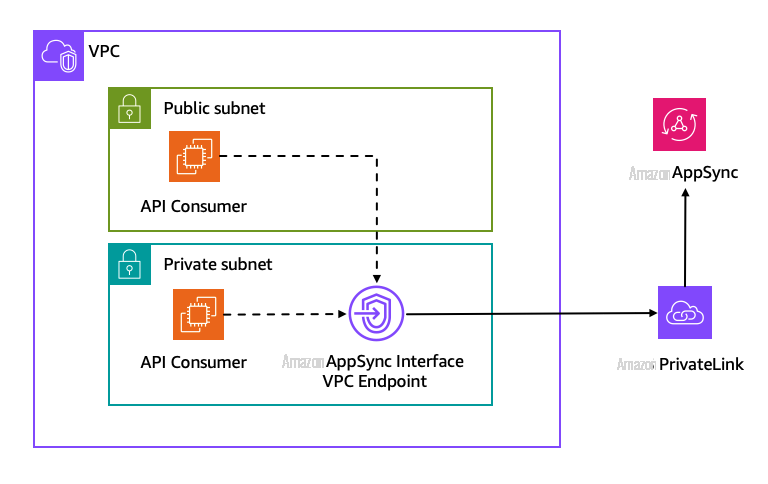
图 2:与 AppSync 私有 API 的单个 VPC 连接
在 VPC 的 CIDR 范围内为 API 使用者和接口终端节点分配私有 IP 地址。默认情况下,每个路由表都包含用于在 VPC CIDR 内进行通信的本地路由。接口 VPC 端点 DNS 名称和 AppSync API GraphQL 端点(启用私有 DNS 名称)将解析为 亚马逊云科技 AppSync 接口端点的私有 IP 地址。这将确保对私有 API 的请求通过接口端点路由到 AppSync 私有 API。
模式 2:跨 VPC 连接到 AppSync 私有 API
在这种模式 中,API 使用者托管在与托管 AppSync VPC 接口终端节点的 VPC 分开的 VPC 中,位于同一 亚马逊云科技 账户中,两个 VPC 位于相同或不同的 亚马逊云科技 区域。您可以使用此模式通过单个 VPC 集中访问您的 AppSync 私有 API,这有助于简化 API 的安全性和访问要求。但是,重要的是要从成本和安全的角度比较集中式和分散式接口端点的设计,正如本次re: Invent演讲、
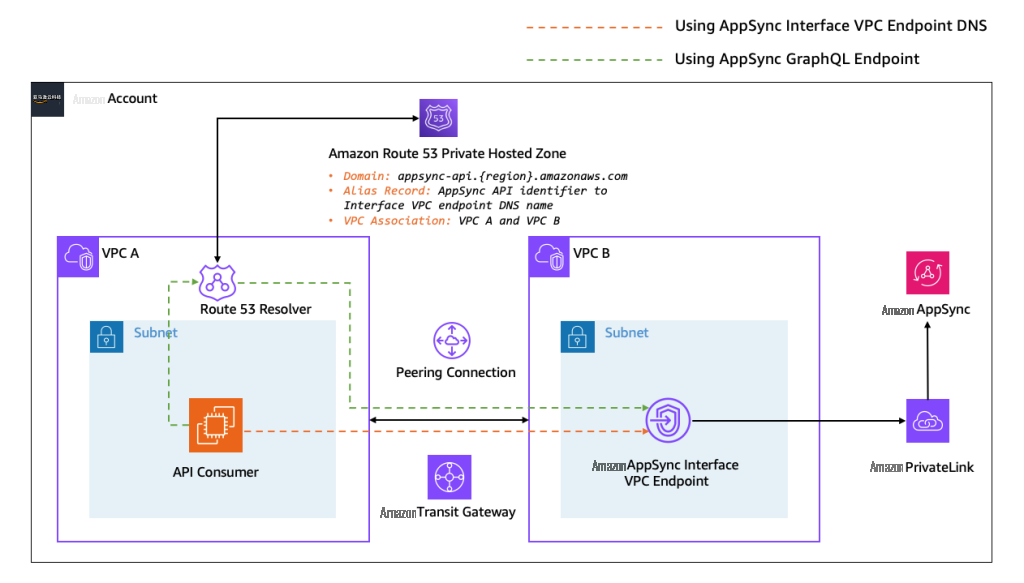
图 3:通过 VPC 连接到 AppSync 私有 API
要开始使用这种模式,请在一个 VPC(集中式 VPC)中创建 AppSync 接口终端节点,然后使用 VPC 对
如果您使用 AppSync 接口终端节点 DNS 名称来调用 AppSync 私有 API,则 VPC A 中的 API 使用者 无需任何其他配置 即可通过 VPC B 中的 AppSync 接口 VPC 终端节点访问私有 API。
使用 AppSync API GraphQL 端点调用私有 API 需要以下配置:
- 关闭 VPC B 中的 “私有 DNS 名称”。这将删除将 AppSync 服务域名的请求解析为 AppSync 接口端点创建的弹性网络接口 (ENI) 的私有 IP 地址的 DNS 条目。
-
创建其中区域设置为 托管 AppSync 接口终端节点的 VPC B 区域。在创建 PHZ 时,将 VPC A 和 VPC B 与托管区域相关联,您可以在 亚马逊云科技 账户内的任何区域中选择任意 VPC。将 VPC 关联到 PHZ 将确保使用 PHZ 中的 DNS 条目解析对 AppSync 服务域的任何请求。亚马逊 Route 53 私有托管区域 (PHZ),将域设置为 AppSync 服务域 appsync-api。{区域} .amazonaws.com
-
<li style="list-style-type: none"></li>
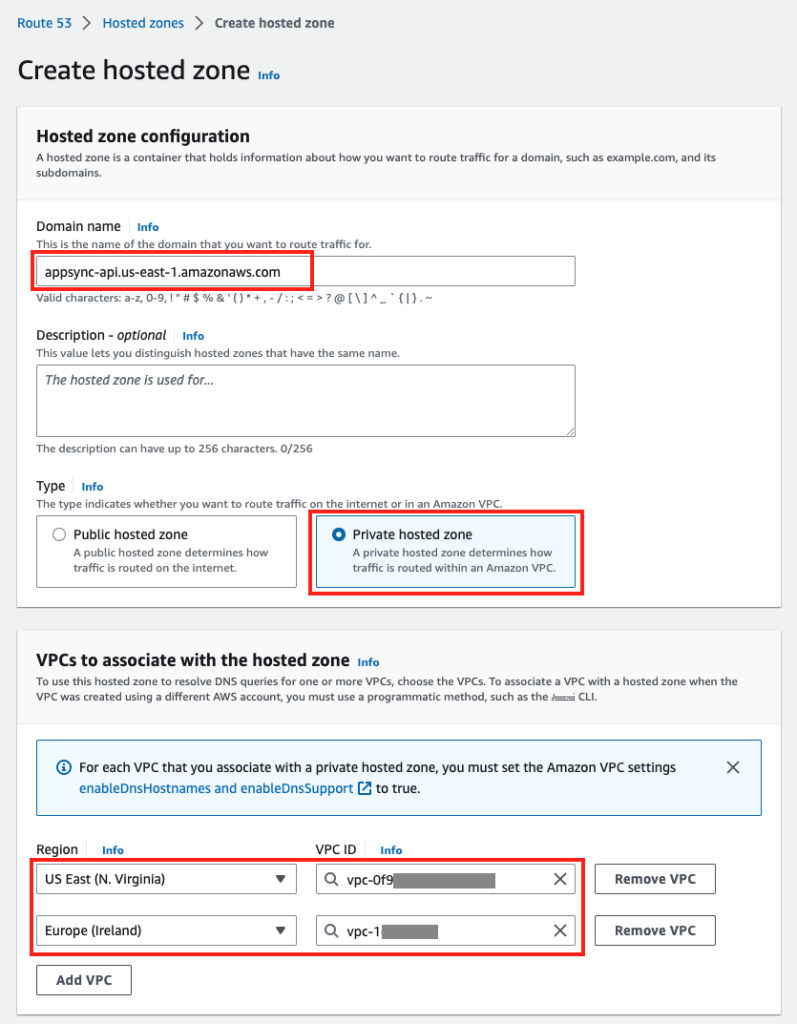
图 4:创建私有托管区域
-
创建 PHZ 后,创建别名 DNS 记录,其名称设置为 AppSync API GraphQL 端点标识符 (
{api_url_identifient} .appsync- ap i。{区域} .amazonaws.com/graphql)和目标设置为 AppSync 接口终端节点,如下所示。有了这些设置,可以 使用 AppSync API GraphQL 终端节点从 VPC A 或 V PC B 调用 AppSync 私有 API。
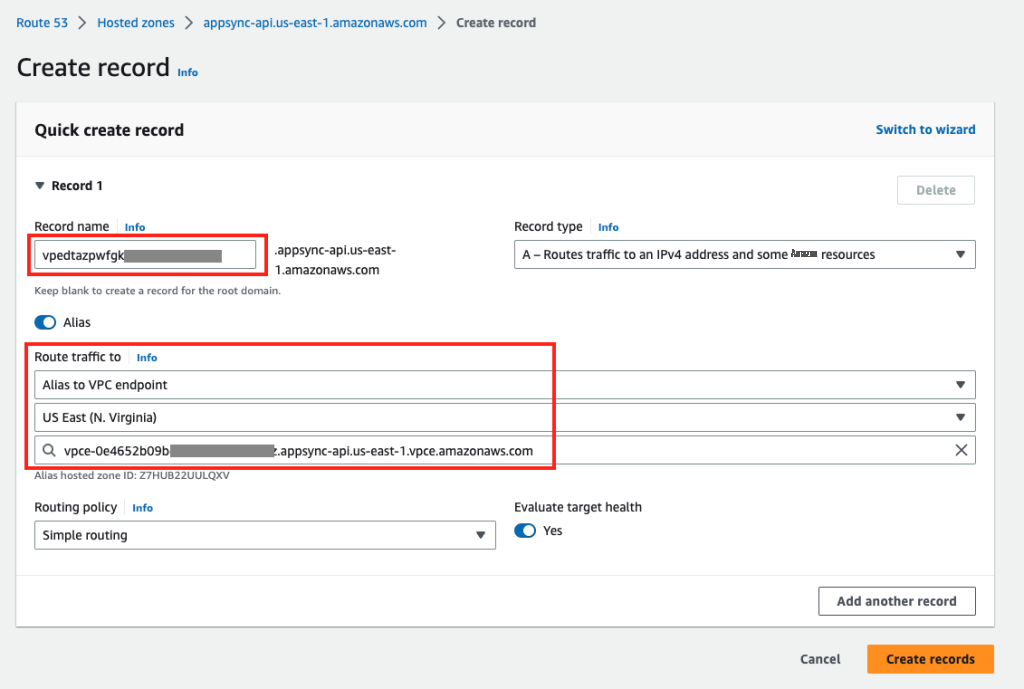
图 5:创建托管区域 DNS 记录
模式 3:与 AppSync 私有 API 的跨账户连接
在这种模式 中,API 使用者托管在与托管 亚马逊云科技 AppSync 接口终端节点(账户 B)不同的 亚马逊云科技 账户(账户 A)中,两个 VPC 位于相同或不同的 亚马逊云科技 区域。在此用例中,您将工作负载分成不同的 亚马逊云科技 账户,使用一个专用账户作为 API 账户(账户 B)。对 AppSync 私有 API 的请求必须通过 API 账户中的 AppSync 接口端点路由到 AppSync 服务。
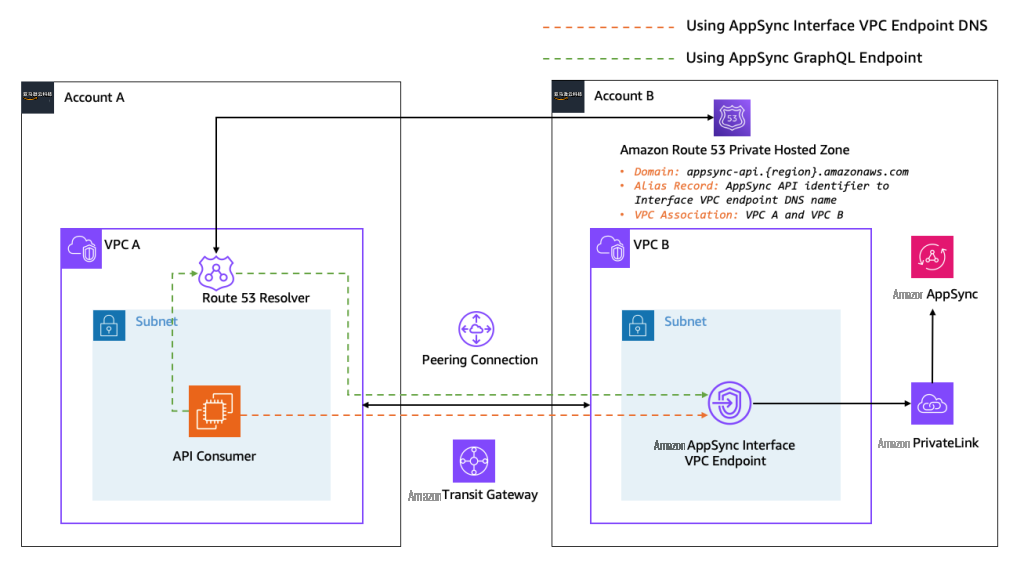
图 6:与 AppSync 私有 API 的跨账户连接
与 模式 2 类似 ,在其中一个 亚马逊云科技 账户中创建一个 AppSync 接口 VPC 终端节点,然后使用 VPC 对等连接或 亚马逊云科技 Transit Gateway 连接这两个 VPC,如上图所示。这将确保 VPC A 中的 API 使用者 可以到达 VP C B 中的 AppSync 接口终端节点。
使用 AppSync 接口终端节点 DNS 名称调用 API, VPC A 中的 API 使用者无需任何其他配置 即可访问私有 API。但是,如果您使用的是 AppSync API GraphQL 端点,则需要按照上面 模式 2 中说明的步骤进行操作。唯一的区别是 VPC 与 PHZ 的关联,这只能通过 CLI 或 SDK 来完成。以下是您需要在 CLI(例如 CloudShell)中完成的步骤,才能将 VPC A 关联 到 PHZ。
- 在 账户 B 中打开 CloudShell 终端节点与托管 AppSync 接口终端节点的 VPC 位于同一区域,然后运行以下命令列出可用的托管区域。记下您要与账户 A 关联的 账户 B 中的托管区域 ID。 托管区域
- 在 账户 B 中的 VPC B 所在区域的 CloudShell 终端 中运行以下命令。 此命令授权 账户 B 中的 PHZ 与账户 A 中的 VPC 之间的关联。 使用上一步中的托管区域 ID、 账户 A 中的 亚马逊云科技 区域和该 VPC 的 ID。
- 在 账户 A 中打开 CloudShell 终端 并运行以下命令。 此命令创建 账户 B 中的 PHZ 和账户 A 中的 VPC 之间的关联。 使用步骤 1 中的托管区域 ID、 账户 A 中的 VP C A 的区域和 VPC ID 。
- PHZ 与 VPC 关联并传播更改可能需要几分钟。还建议您在使用此命令创建关联后删除关联。
- 在 账户 B 的 Route 53 控制台中 ,选择 PHZ 并验证 账户 A 的 VPC ID 是否与 PHZ 相关联
将 VPC A 与 PHZ 关联后,按照 模式 2 中的步骤 3 中的说明创建别名 DNS 记录 ,这将完成配置。现在,你可以 使用 AppSync API GraphQL 终端节点从 VPC A 或 V PC B 上调用 AppSync 上的私有 API。
模式 4:与 AppSync 私有 API 的混合连接
在此架构中,采用混合架构,将 API 使用者托管在本地。例如,这些应用程序可以是尚未迁移到 亚马逊云科技 的应用程序,也可以是由于监管或合规要求而需要保留在本地的应用程序。
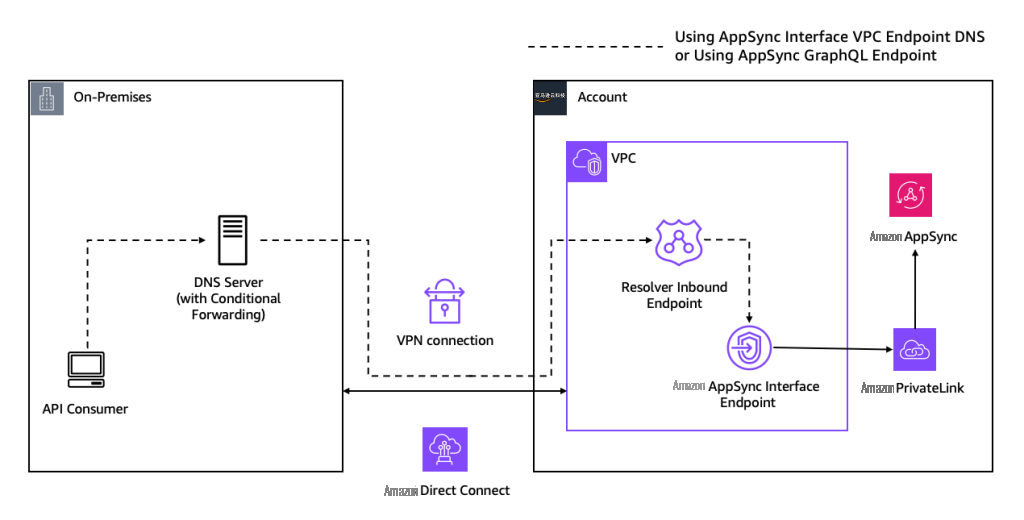
图 7 与 AppSync 私有 API 的混合连接
这种架构模式需要在 亚马逊云科技 和本地站点 之间建立
- 确保 AppSync 接口端点的 “私有 DNS 名称” 已启用。这将确保发往 AppSync GraphQL 端点的请求通过 AppSync 接口端点路由到 AppSync 私有 API
-
为托管 AppSync 接口端点的 VPC 创建 Amazon Route 53 解析器入站终端节点。您可以按照
文档 获取有关如何创建入站端点的分步指南。您将需要: 为解析器- 入站终端节点 指定名称指定用于部署解析器入
- 站终端节点的 VPC 提供用于终端节点
- 的安全组 指定两个或更多可用区域和子网,从中为解析器入站终
- 端节点分配 IP 地址以进行
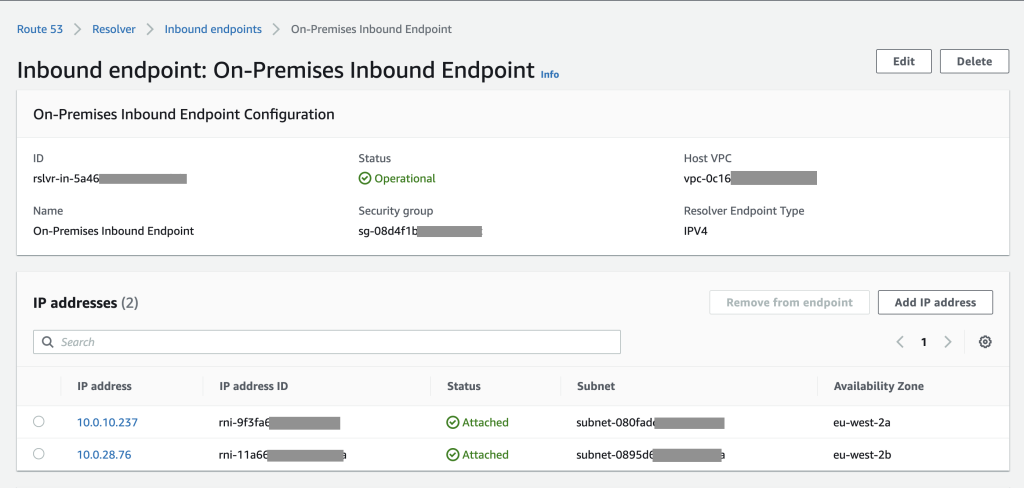
图 8:为入站端点配置 Route 53 解析器
-
在本地环境中,更新 DNS 服务器以将请求转发到 AppSync 接口端点 DNS (appsync-
api)。{区域} .vpce.amazonaws.com )和 AppSync 服务域名(appsync-api。 {区域} .amazonaws.com) 到解析器入站终端节点 IP 地址。使用这些设置,来自本地环境中 API 使用者的 GraphQL 请求将到达 AppSync 接口端点。
模式 5:带有 API 网关的代理 AppSync 私有 API
此模式解决了使用
注意
:此架构模式只能与 AppSync 私有 API 一起使用。如果您的 AppSync API 具有公共端点,请将
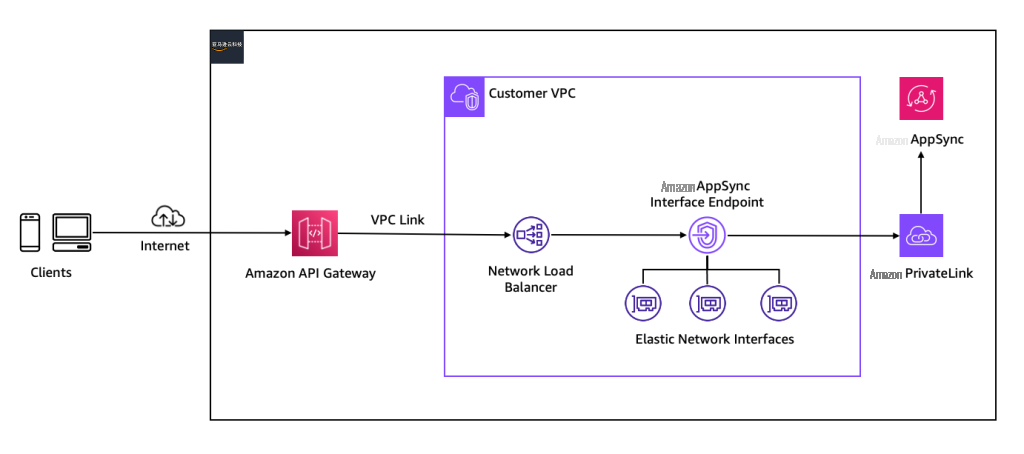
图 9 带有 API 网关的代理 AppSync 私有 API
- 在 AppSync 上创建您的私有 API,并在目标子网上部署 亚马逊云科技 AppSync 接口终端节点。
- 创建网络负载均衡器,将目标设置为 亚马逊云科技 AppSync 接口终端节点的 IP 地址。
-
使用网络负载均衡器作为目标服务创建 VPC 链接、REST API 和私有集成(请参阅
此处 有关如何创建这些资源的指南)。 - 您可以在 API Gateway 上将您的 API 设置为私有、区域或边缘优化 API。在上面的架构图中,我们展示了 API 网关上的区域 API 的设置。
通过这种设置,有权访问 API 网关端点的 API 使用者将能够在 AppSync 上调用私有 API。您可以在
在 AppSync 私有 API
上调用 GraphQL 操作(查询、突变和订阅)调用 AppSync 私 有 API
有两种方法:
-
使用格式为 https://{api_url_identifier}.appsync-api 的 AppSync GraphQL 端点(由 AppSync 生成)。 {区域}.amazonaws.com/graphql -
使用 AppSync 接口端点 DNS(这是为 AppSync 接口端点生成的,格式为 https://{vpc_endpoint_id}-{endpoint_dns_identifier}.appsync-api。{区域} .vpce.amazonaws.com/graphql
对于希望在调用私有 API 和非私有 API 时保持相同应用程序配置的客户,建议使用 AppSync GraphQL 端点。但是,如果在某些用例中,API 使用者需要从 VPC 调用私有 API 和非私有 API,则需要在非私有 API 上配置
这是因为开启私有 DNS 的 AWS AppSync 接口终端节点会将所有流量路由到目标 *.appsync-api。{区域} .amazonaws.com/graphql
通过 亚马逊云科技 AppSync 的 接口终端节点,非私有 API 将被屏蔽。
使用 AppSync 接口端点 DNS,可以将 API 使用者配置为调用 AppSync 私有 API,这将通过接口端点路由流量。使用 AppSync 接口端点 DNS 时,可以在接口端点上关闭 “私有 DNS 名称”。API 使用者可以使用 API AppSync GraphQL 端点调用其他非 AppSync 私有 API,无需配置 AppSync 自定义域。
要使用 AppSync GraphQL 端点调用您的私有 API 进行查询和突变,请参阅以下示例
而且你可以使用 GraphQL 实时端点设置订阅,例如以下用于建立 websocket 连接的命令:
以下示例显示如何使用 AppSync 接口终端节点 DNS 调用私有 API 进行查询和突变。您需要将 AppSync GraphQL 端点设置为请求的主机或 x-appsync 域标头。
并且你可以使用 AppSync 接口终端节点 DNS 设置订阅,如以下示例所示,
结论
在这篇博客中,我们介绍了访问您的 亚马逊云科技 AppSync 私有 API 的五种架构模式。这些模式将帮助您识别 API 使用者的架构和配置,以便安全地访问您的私有 API。您还可以将其中两种或更多种架构模式组合成一个架构,以满足不同位置的 API 使用者的需求。有关更多详细信息,请参阅
作者简介
*前述特定亚马逊云科技生成式人工智能相关的服务仅在亚马逊云科技海外区域可用,亚马逊云科技中国仅为帮助您发展海外业务和/或了解行业前沿技术选择推荐该服务。